(rev. Mar 13, 2017)
Notes On Chapter Thirteen
-- Local Area Networks: Packets, Frames and Topologies
- 13.0 Study Guide
- Understand the concept of packet switching, what are its advantages,
and how it differs from circuit switching.
- Understand what the data link layer is, and where it is located in the
TCP/IP protocol stack
- Have some familiarity with the IEEE family of 802.x standards for LANs.
- Be familiar with the major LAN topologies
- Know the basics of the IEEE 48-bit MAC addressing scheme
- Understand what unicast, broadcast, and multicast addresses are
- Know the typical structure of a frame in a packet-switched LAN
- 13.1 Introduction
- IEEE Standards Model
- Hardware Addressing
- Frame Identification
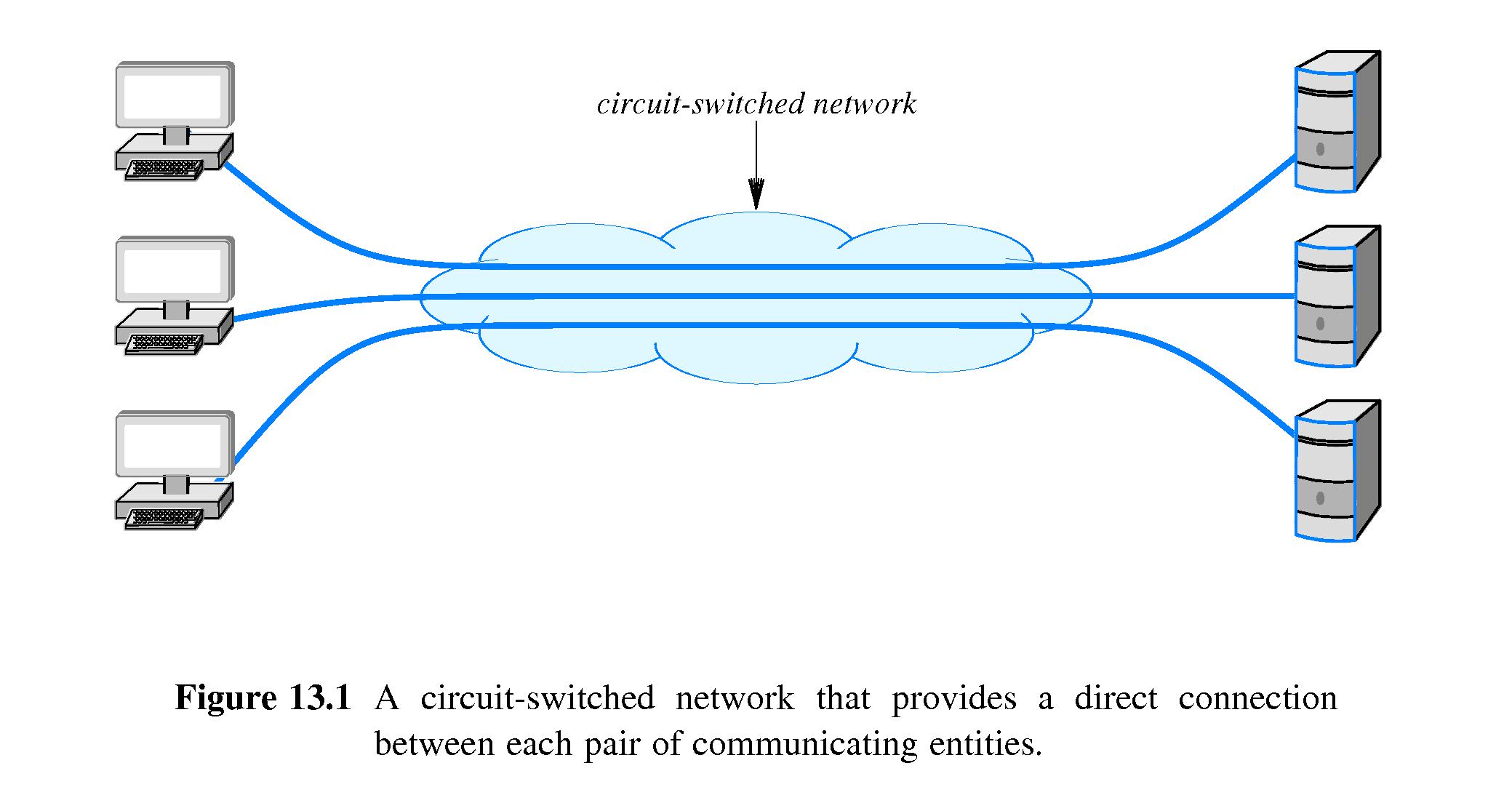
- 13.2 Circuit Switching
-
Circuit switching is: "a communication mechanism that establishes a
path between a sender and a receiver with guaranteed isolation from
paths used by other pairs of senders and receivers.
- Nowadays circuits are virtual - multiplexed over shared media
-
The properties that define a circuit switched paradigm
- Point-to-point communication
- Separate steps for circuit creation, use and termination
- Performance equivalent to an isolated physical path
(virtual circuits use FDM or synchronous TDM. )
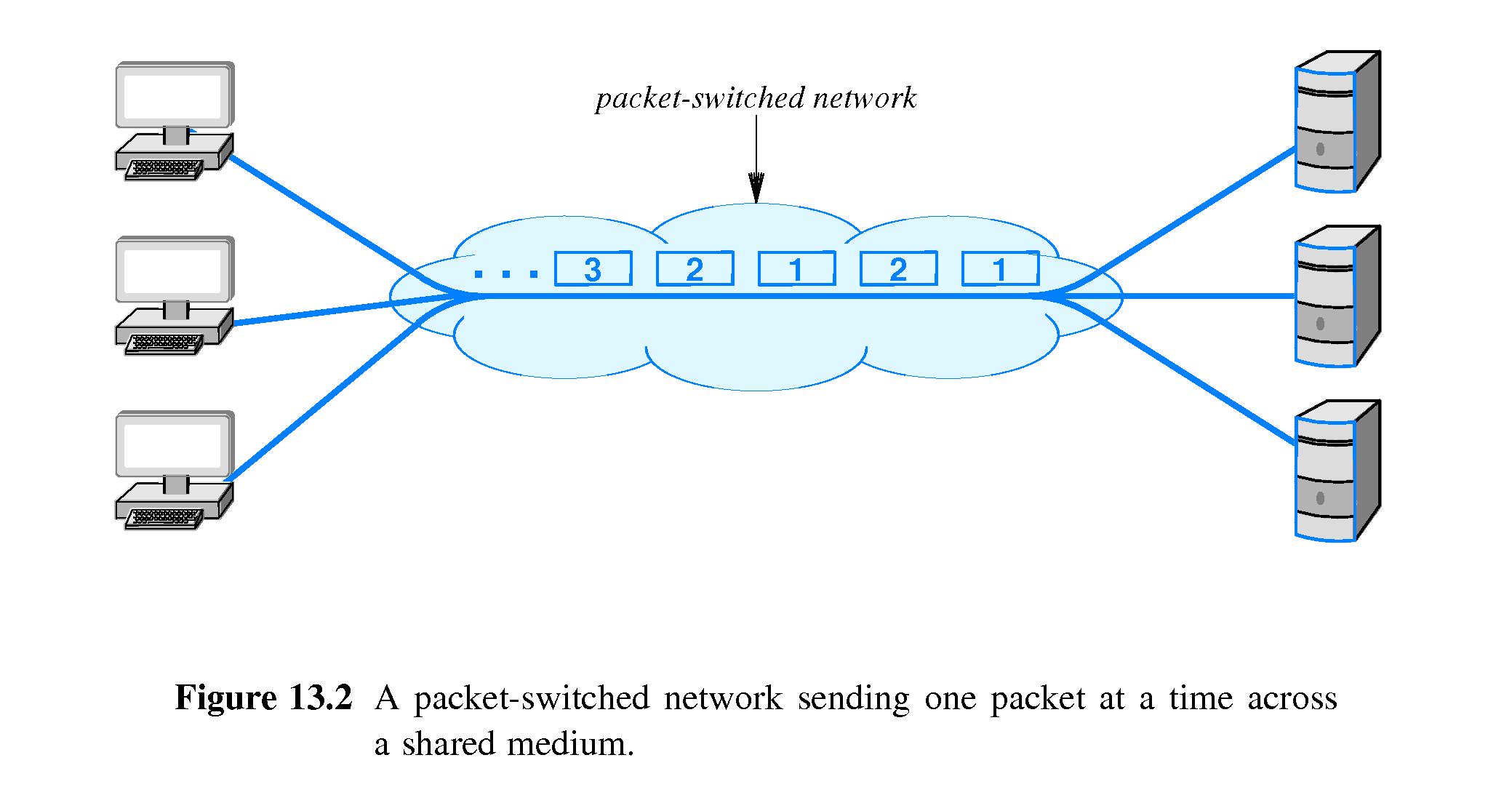
- 13.3 Packet Switching
- Packet switching uses statistical multiplexing.
- Senders must divide their messages into small blocks of data
(packets).
-
Properties that define a packet-switched paradigm
- Arbitrary, asynchronous communication (implies many-to-many
communication)
- No set up required before communication begins
- Performance varies due to statistical multiplexing among packets
- Packet switching allows senders to send to multiple recipients
concurrently, and allows receivers to receive from multiple
senders concurrently.
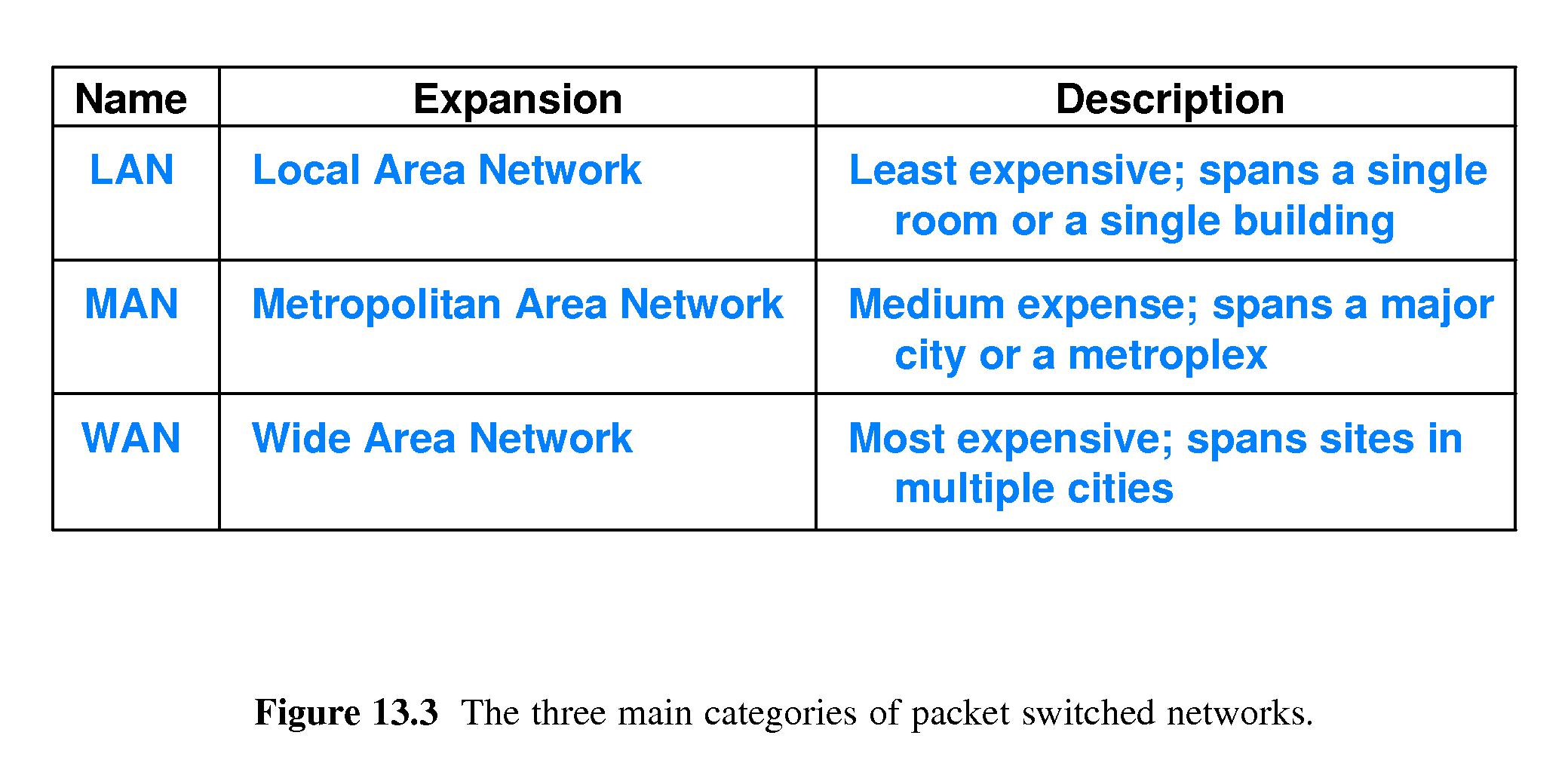
- 13.4 Local and Wide Area Packet Networks
- LAN - Local Area Network - least expensive - spans
single room or building
- MAN - Metropolitan Area Network - Medium expense - spans major city
or metroplex
- WAN - Wide Area Network - Most expensive - spans sites in multiple
cities
- 13.5 Standards For Packet Format and Identification
- Packets have to contain the address of the intended recipient.
-
Protocols have to stipulate the form of address and placement of the
address in the packets.
- The Institute for Electrical and Electronic Engineers (IEEE) created
the most widely used set of LAN standards.(Project 802 LAN/MAN
Standards Committee, 1980)
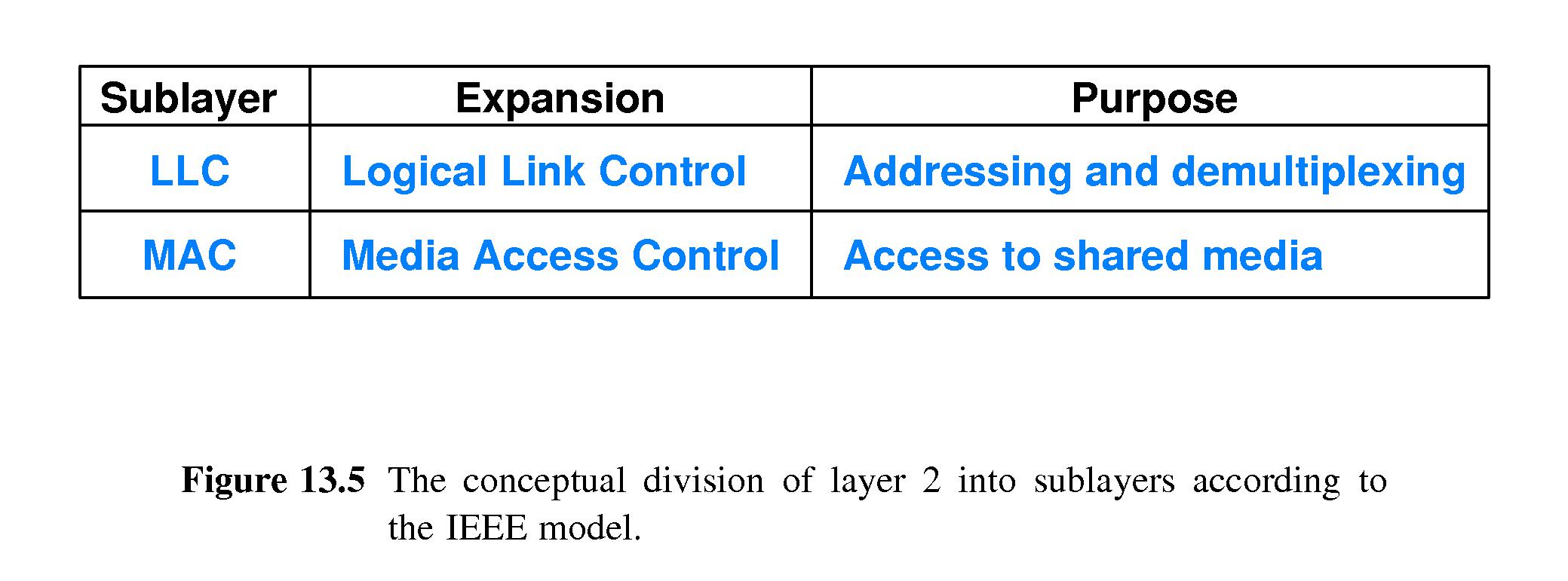
- 13.6 IEEE 802 Model and Standards
- IEEE divides the Data Link layer into two sub-layers.
- The Logical Link Control sub-layer specifies addressing and the use
of addresses for demultiplexing.
- The Media Access Control sub-layer specifies how a group of computers
share the medium.
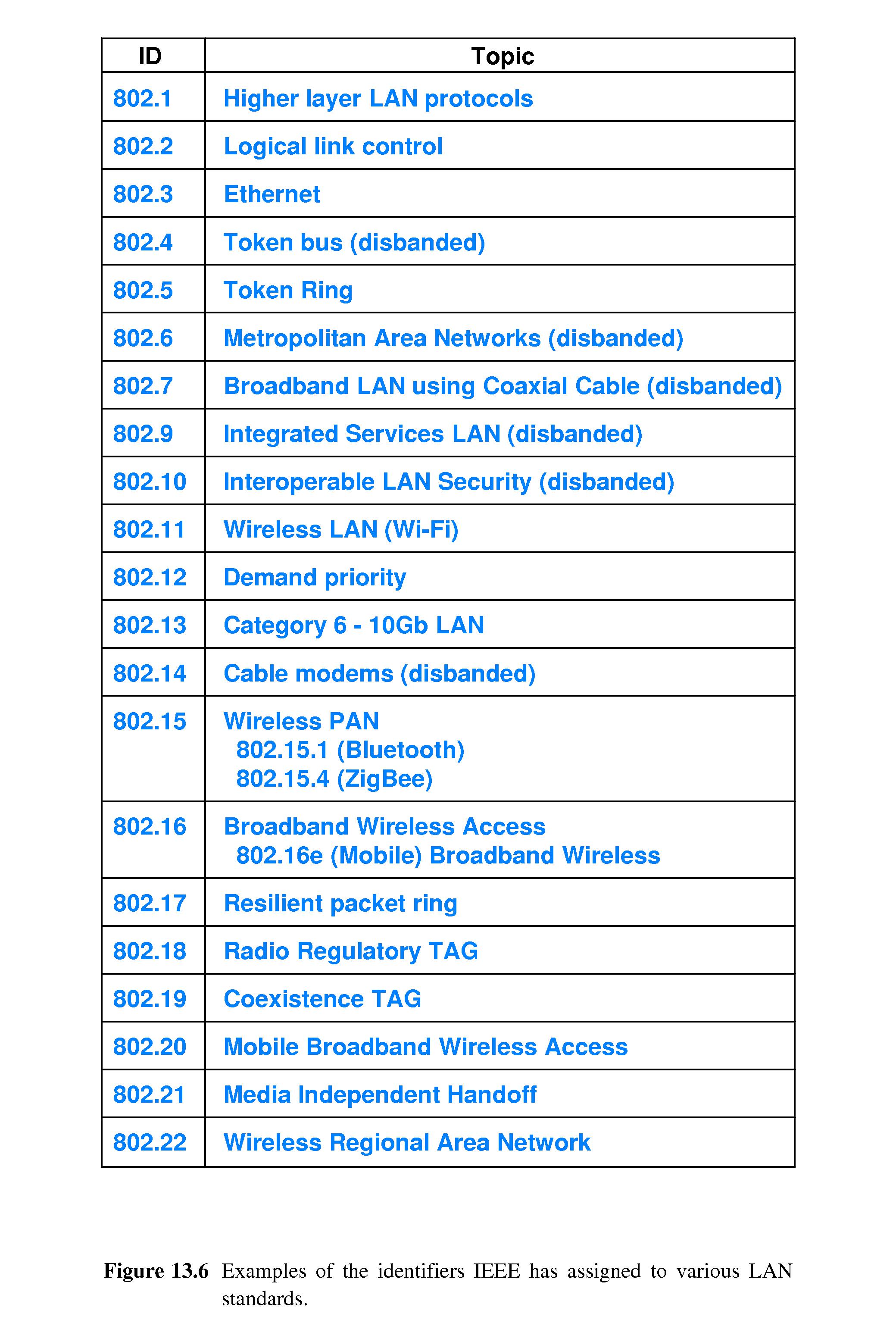
-
The LAN protocols are numbered starting with the suffix 802.
- 13.7 Point-to-Point and Multi-Access Networks
- In a multi-access network,
many computers share a medium in a way
that allows any pair to communicate.
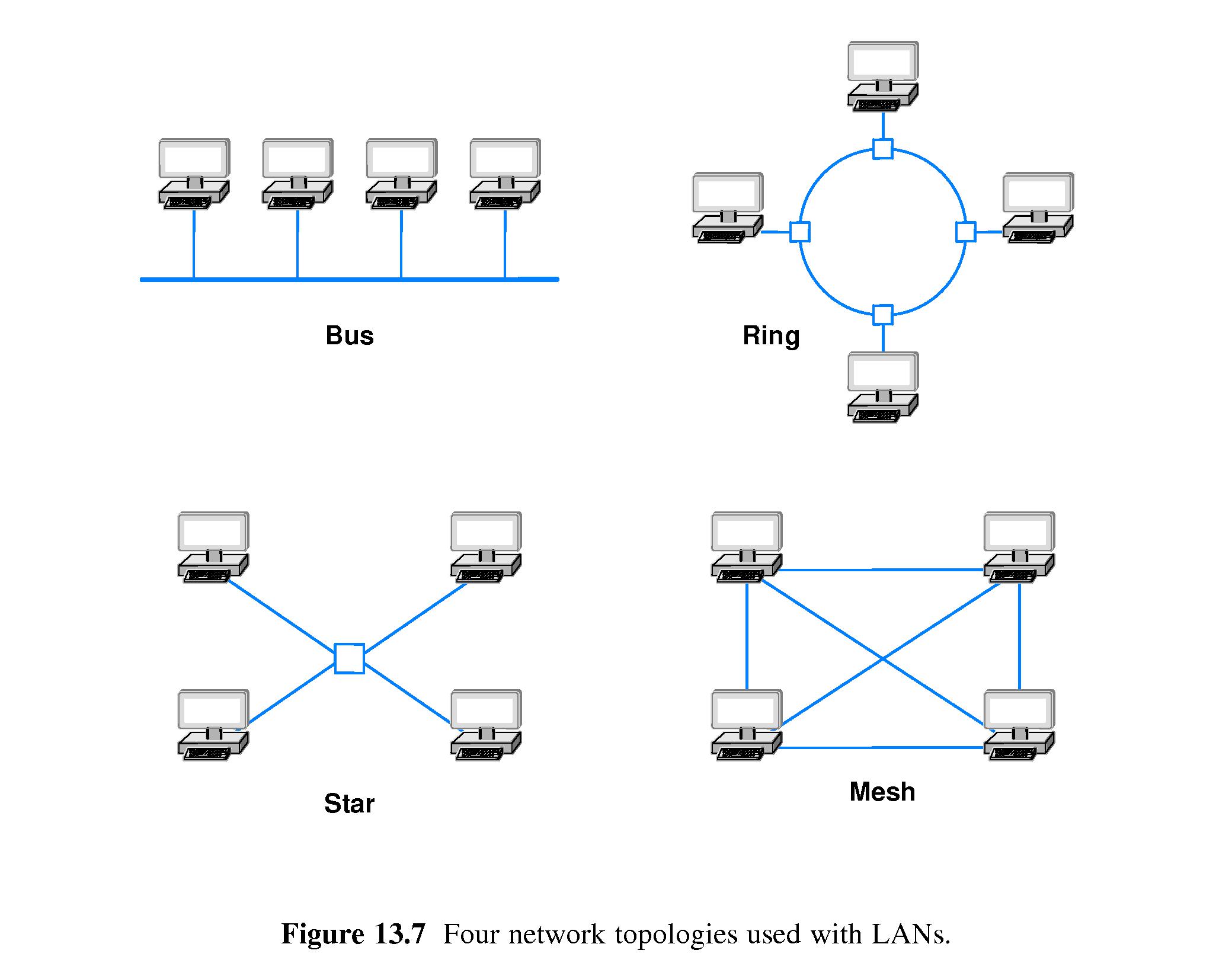
- 13.8 LAN Topologies
- 13.8.1 Bus Topology
- All computers attach to a single cable or other medium
- When a computer sends, all can receive.
- A protocol is needed to handle collisions
- (may resemble a star topology)
- 13.8.2 Ring Topology
- Computers connected in a "chain", plus the last connected back
to the first.
- (may resemble a star topology)
- 13.8.3 Mesh Topology
- A direct connection between each pair of computers
- High performance is possible.
- This is very expensive except for very small networks.
- 13.8.4 Star Topology
- All computers attach at one "central" point.
- 13.8.5 The Reason For Multiple Topologies
-
Each topology has advantages and disadvantages
- In a ring it is easy to coordinate access and tell whether a
link is down. If one link is down the entire network is
disabled.
- A link lost in a star cuts off only one host from the network.
- A bus network is inexpensive but everything depends on the one
bus working.
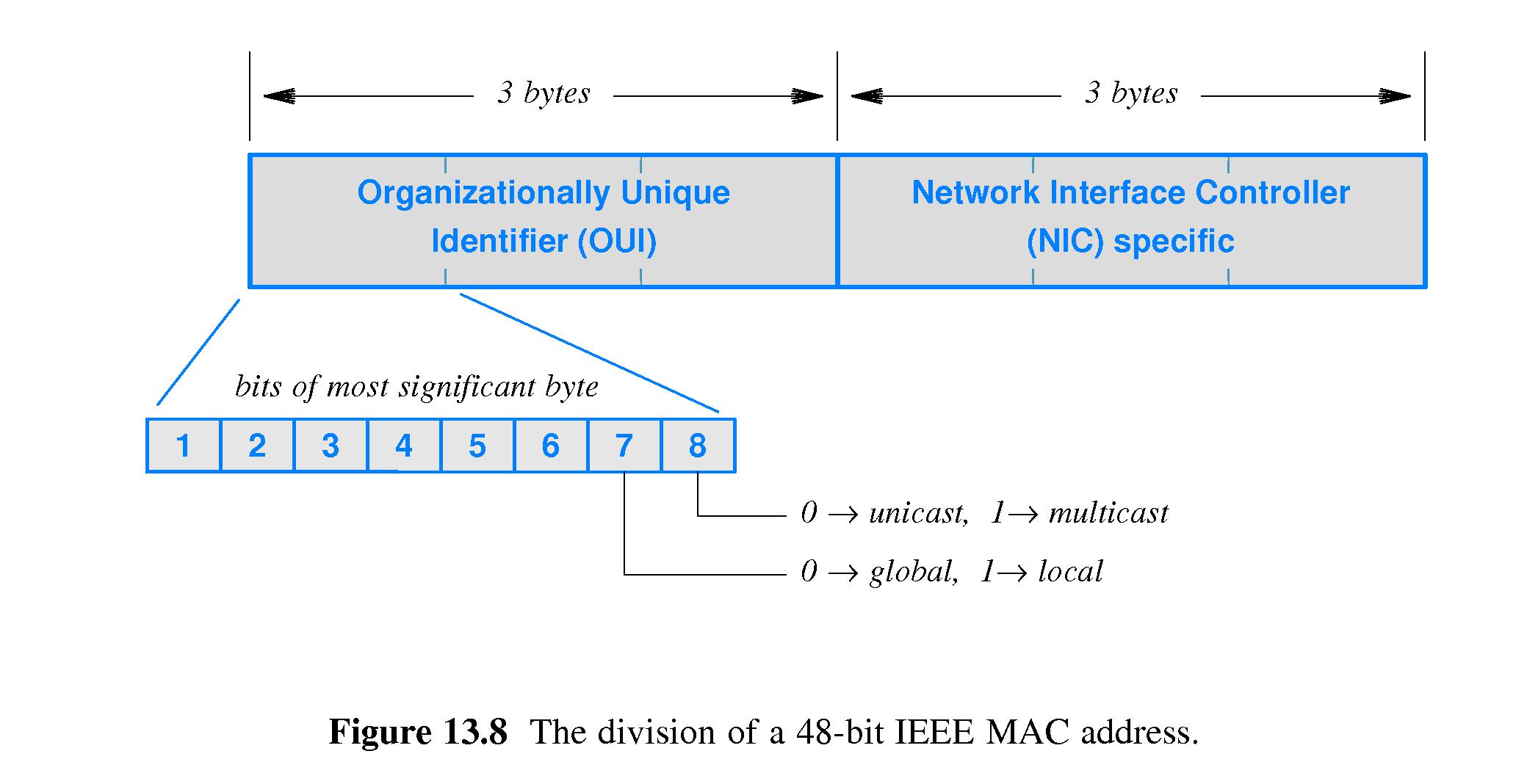
- 13.9 Packet Identification, Demultiplexing, MAC Addresses
- IEEE created an addressing standard for LANs
- Under the standard,
each NIC is assigned a unique 48 bit address
- Each packet sent on the LAN is required to contain the address of the
intended recipient of the packet.
- These 48-bit IEEE addresses are called Media Access Control (MAC)
addresses. They are also called Ethernet addresses, because they
originated with the development of Ethernet technology.
- IEEE regulates the allocation of Ethernet addresses to make sure that
NIC's manufactured by vendors are assigned unique addresses.
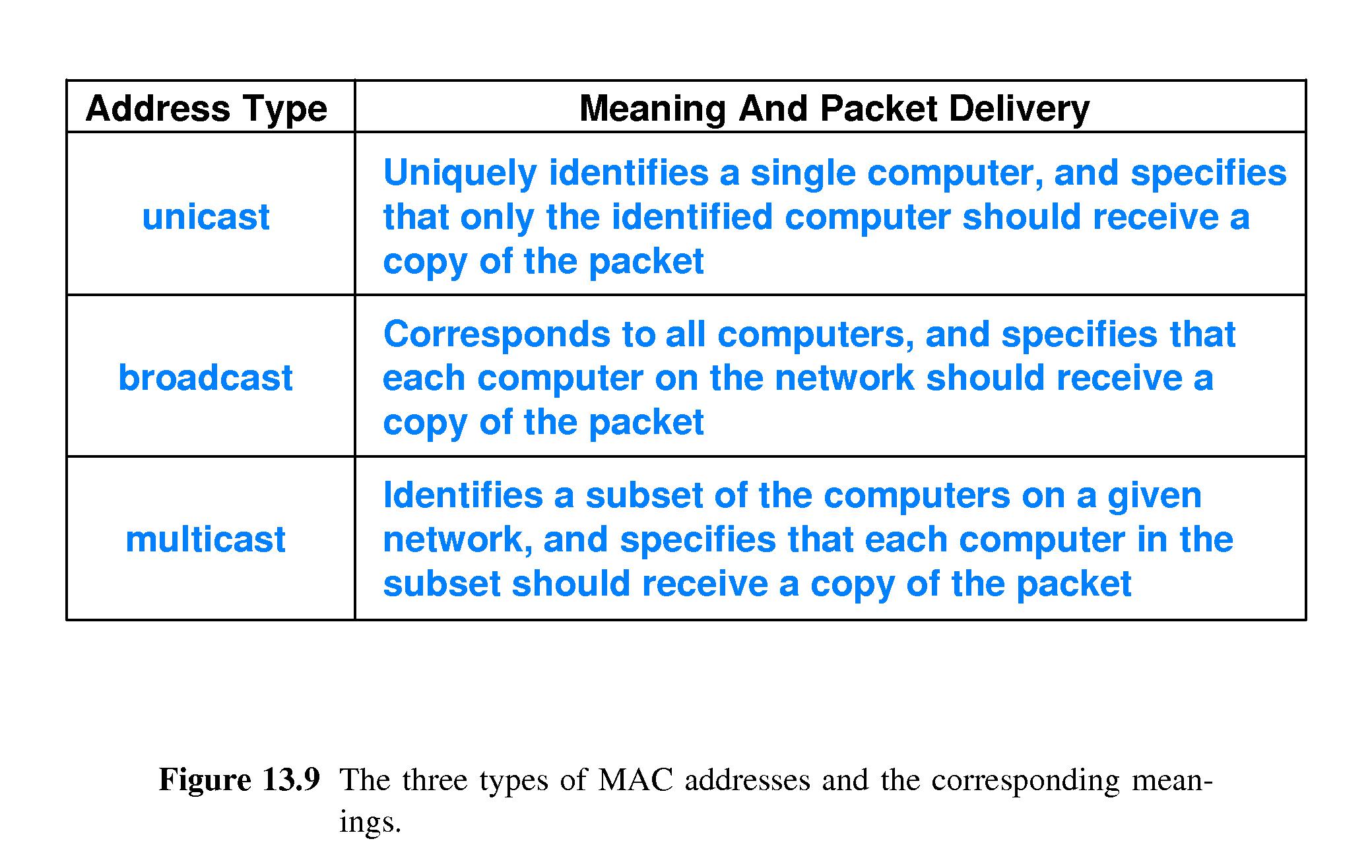
- 13.10
Unicast, Broadcast and Multicast Addresses
- There are three types of IEEE MAC (Ethernet) addresses:
- Unicast - for sending a packet to exactly one recipient
- Broadcast - for sending a packet to be delivered to every NIC on
the network. The broadcast address is "all 1's"
- Multicast - for sending a packet to each of a specific set of
NIC's
- 13.11 Broadcast, Multicast and Efficient Multi-Point Delivery
- Broadcast and Multicast are relatively efficient
on a shared-medium LAN such as Ethernet, because a sender puts
only a single copy of the packet on the LAN.
- All packets placed on the LAN are monitored by every NIC connected to
the LAN.
- The NIC examines the address of each packet
- If the address is "a match" the NIC "accepts" the packet.
- The address matches if:
- it is the (unique) MAC address of the NIC, or if
- it is the broadcast address, or if
- it is the multicast address of a multicast group to which the
NIC belongs.
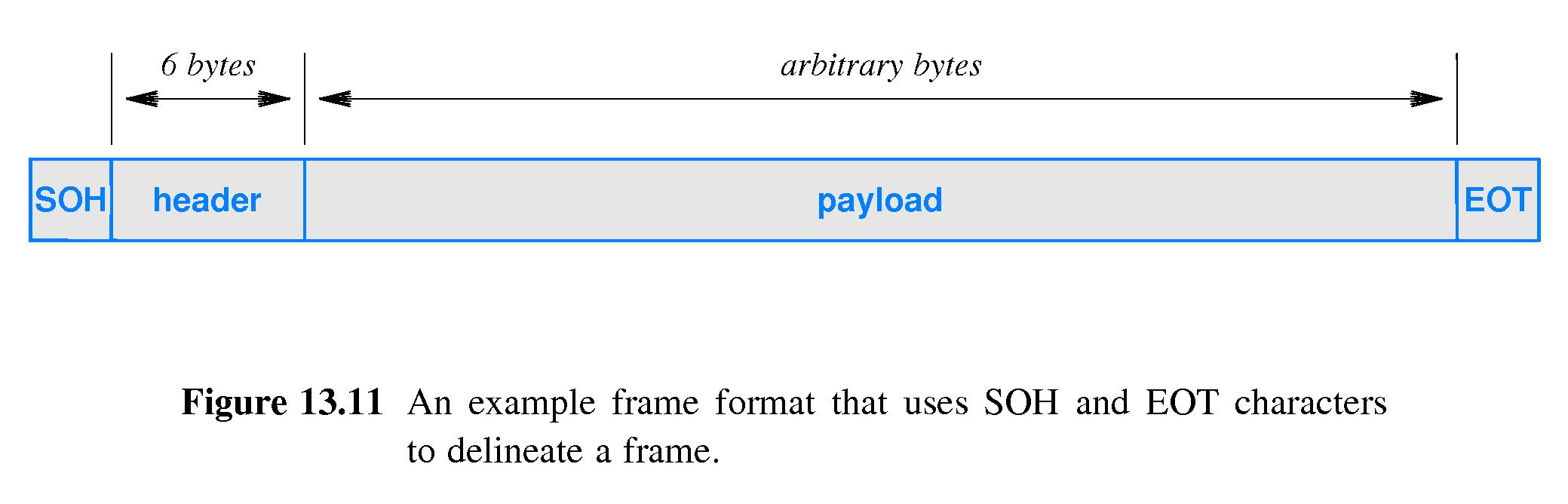
- 13.12 Frames and Framing
- Typically a header is added to a packet
and sent with it on the network
- Headers contain things like the address of the intended recipient,
a check sum, and other metadata.
- Typically the packet header is sent first, followed immediately by
the packet 'payload' - actual message data.
- Sometimes a short 'prelude' (prolog) is sent just before the header,
and sometimes a short 'postlude' (epilog) after the payload.
- The prelude and postlude can be helpful when recovering from errors
or synchronizing.

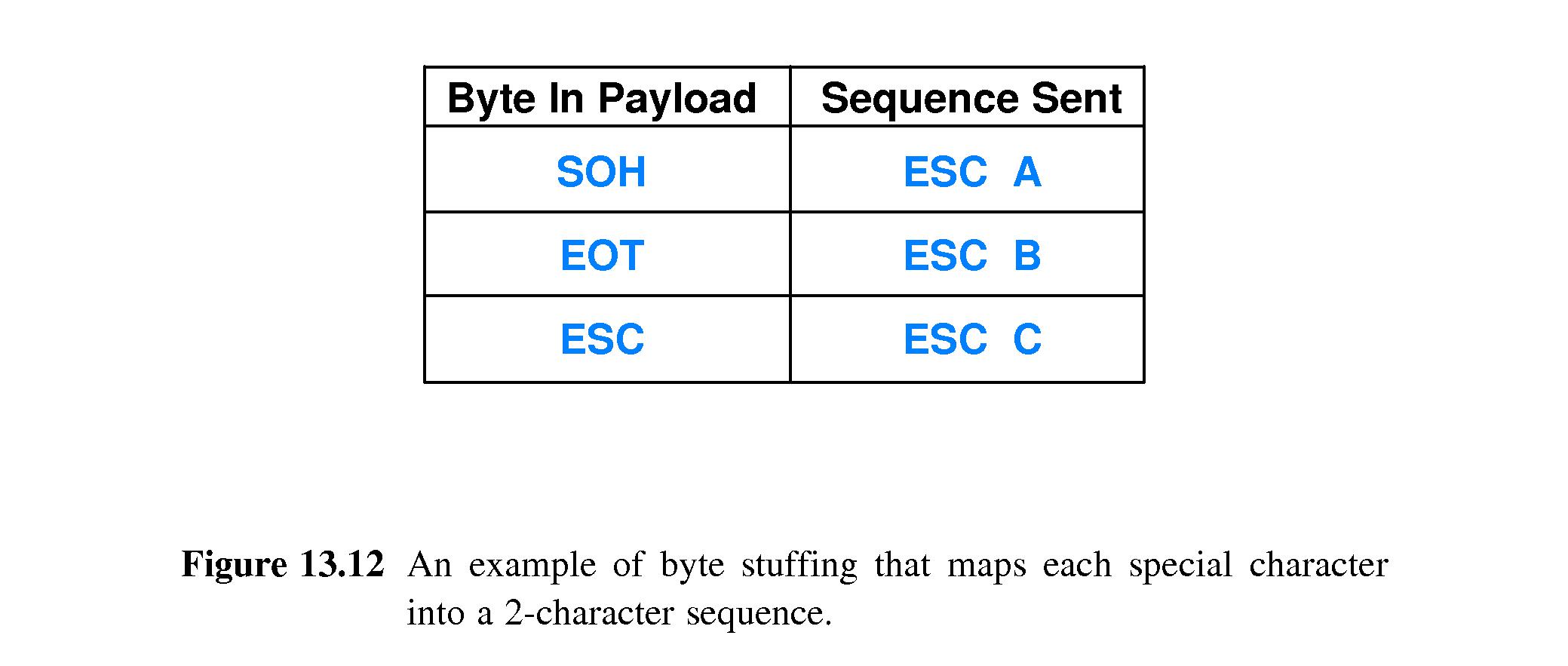
- 13.13 Byte and Bit Stuffing
- Suppose that ASCII SOH and EOT are used as the prelude and postlude.
- Then those characters can't be allowed inside the packet
- If they do occur inside the packet, the sender can do byte stuffing.
- An example is if, before sending, the the sender replaces SOH inside
the packet with ESC-A, EOT with ESC-B, and ESC with ESC-C.
- When the receiver encounters any of {ESC-A, ESC-B, ESC-C} in the
received packet, it replaces them with SOH, EOT and ESC respectively.
- If the sender desires something like ESC B to occur in the data,
there is no problem. ESC B is encoded as ESC C B, and the decoding
scheme works on that sequence properly.