(rev. May 08, 2017)
Notes On Chapter Twenty-Nine
-- Network Security
- 29.1 Introduction
- Types of Internet crime
- Key aspects of security
- Technologies used to increase network security
- 29.2 Criminal Exploits and Attacks
- Scams and ID theft threaten individuals.
- Businesses are concerned about theft, damage to reputation, loss of
customer confidence, stolen intellectual property, and prevention of
customer access.
- Major security problems: Refer to Figure 29.1.
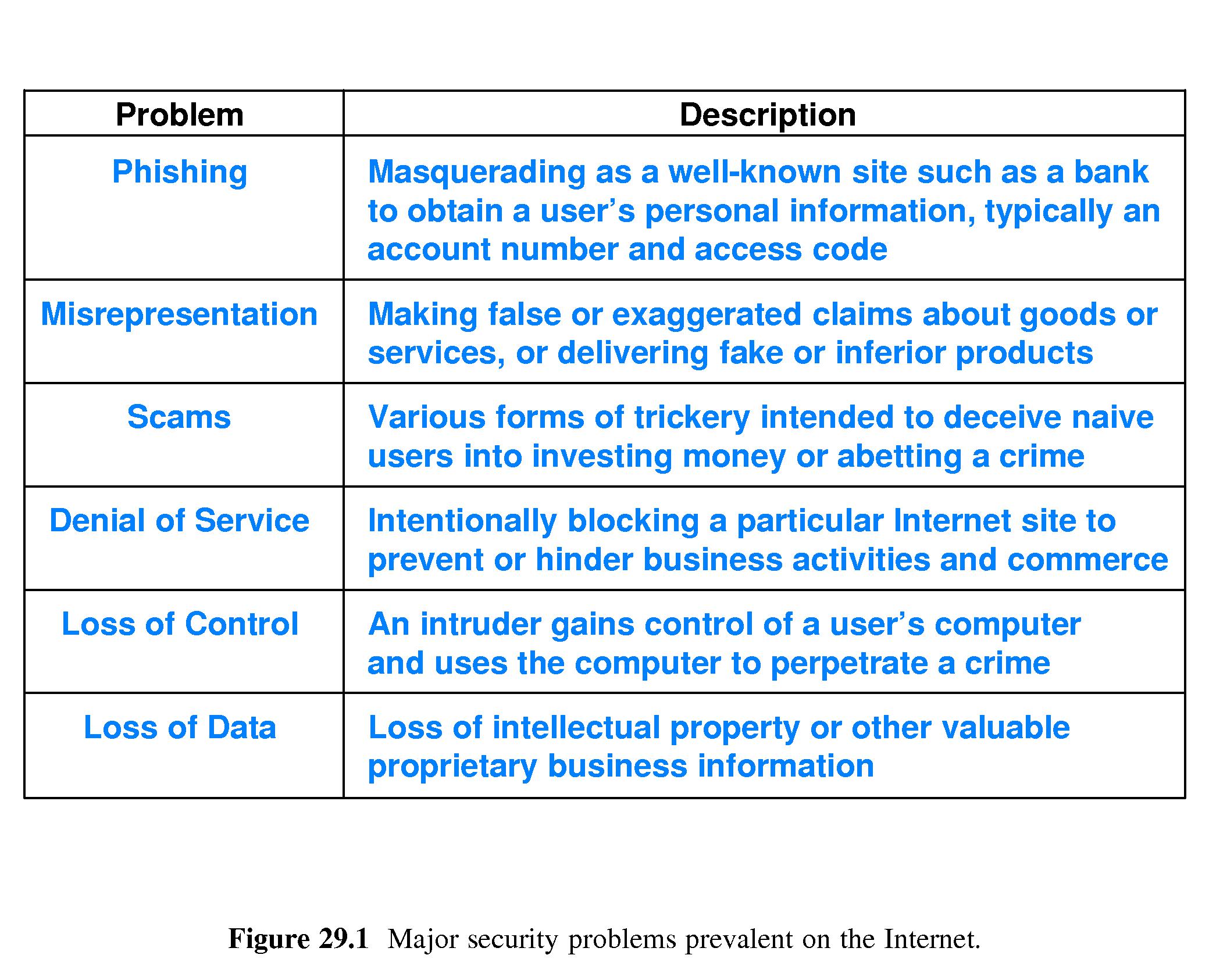
- One must understand the distinction between crime specific to the
Internet and crime that uses the Internet incidentally.
- This discussion focuses on ways criminals exploit network technology,
and on means developed to make such crime more difficult or expensive.
- Specific techniques that attackers use: Refer to Figure 29.2.
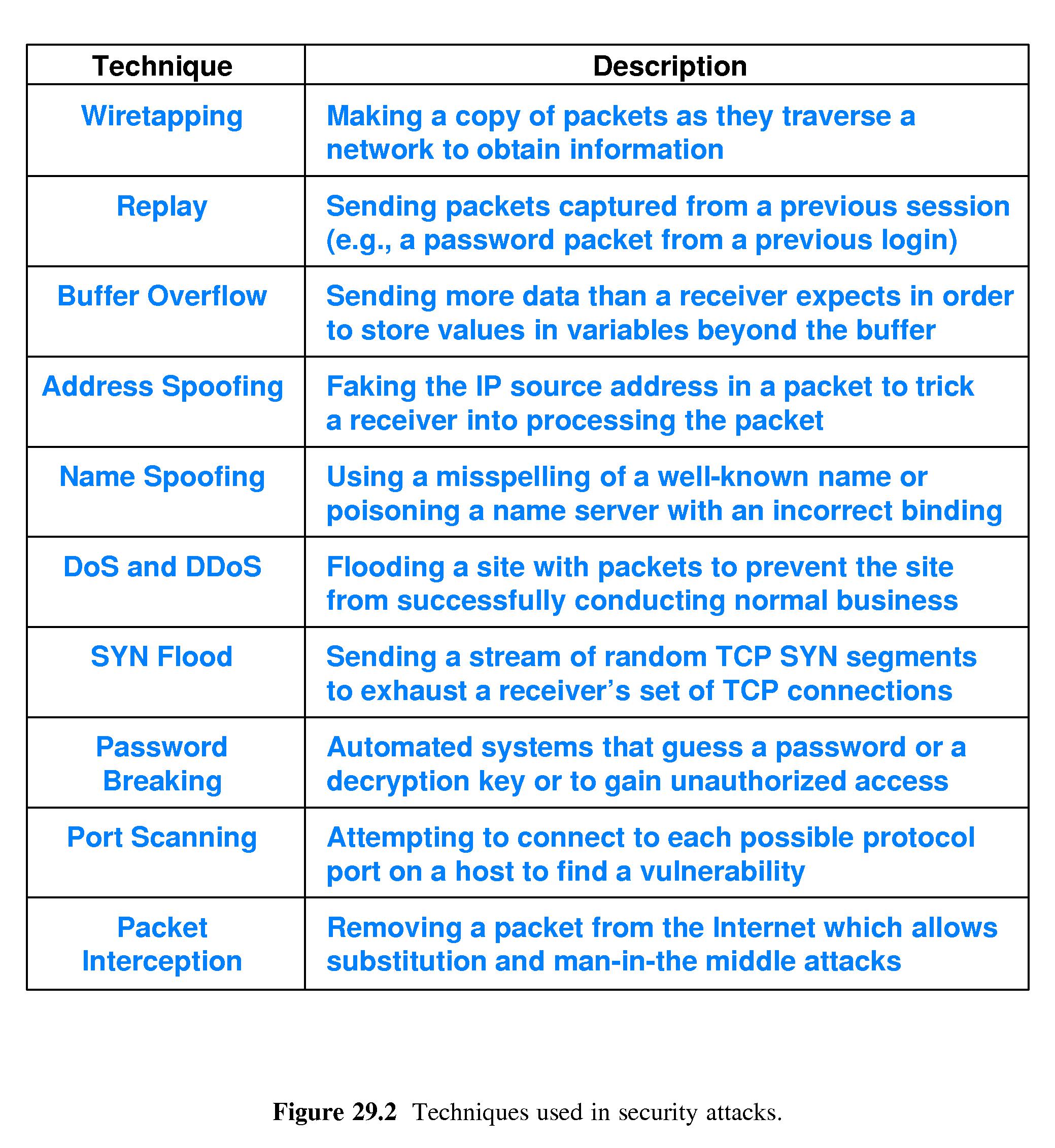
- Buffer overflow is among the most exploited weaknesses.
- Forms of spoofing: broadcast an ARP reply that creates a false
binding, using a routing protocol to send incorrect routes, sending a
DNS message that puts an incorrect binding in a DNS server, and using
a slight misspelling of a well-known domain name to give a user the
impression that s/he has reached a trusted web site.
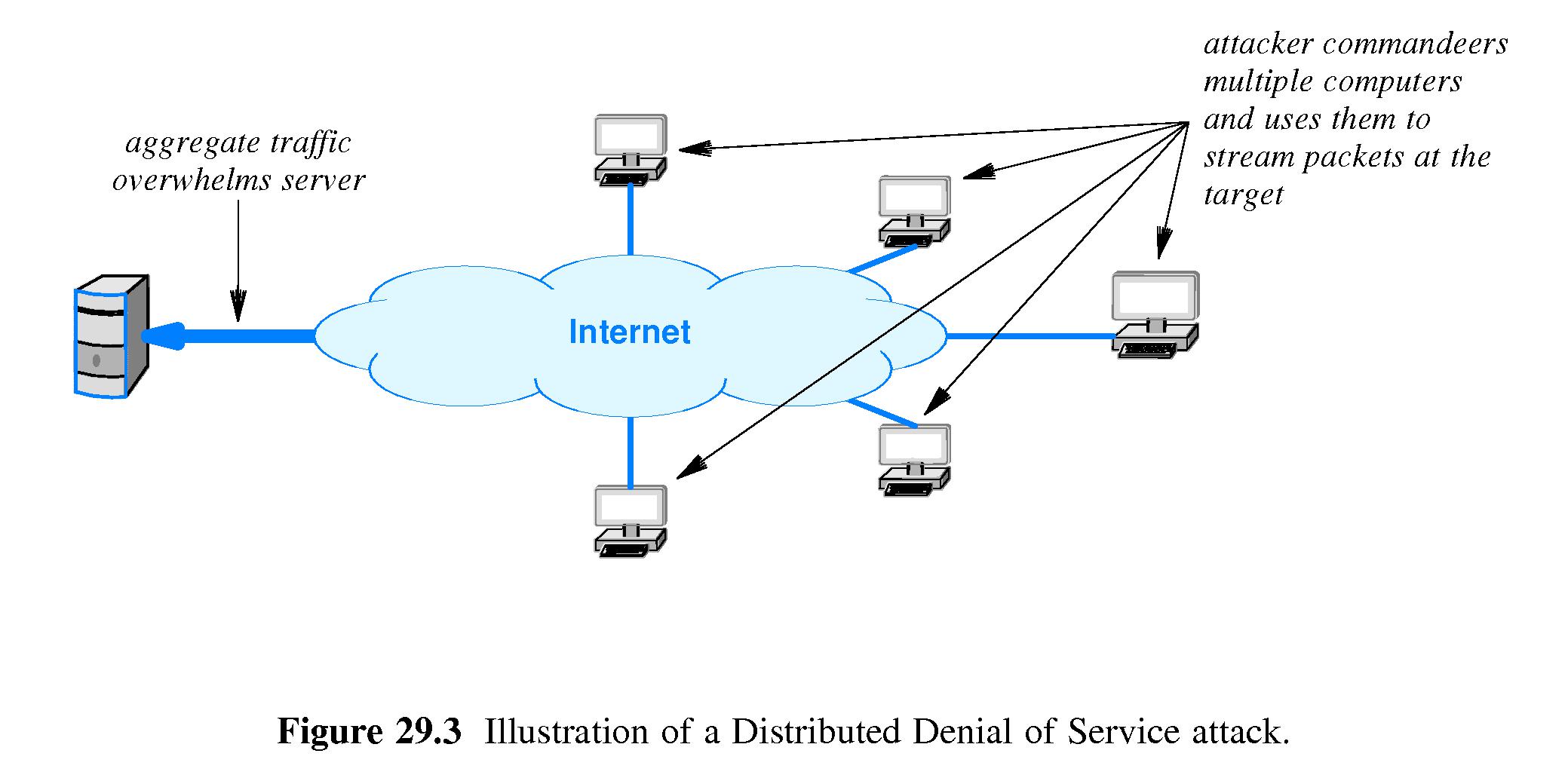
- Distributed Denial of Service attacks arrange for a large set of
hosts to sent excessive traffic to a host victim. Typically the
attacking machines have been previously 'hijacked' and configured to
participate in the attack (Refer to Figure 29.3).
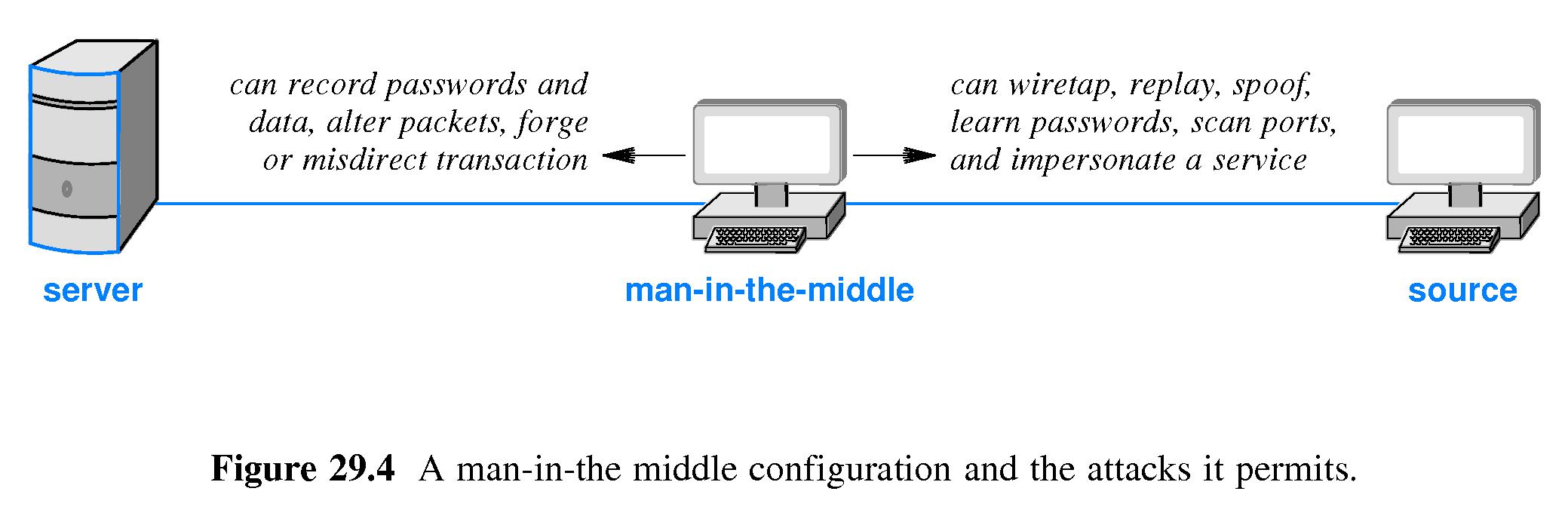
- Man in the middle attacks involve packet interception. They
are very difficult to engineer but their potential to do harm is
exceptional.
- 29.3 Security Policy
- Security means different things to different people.
- Different people and organizations have different security needs.
- It is important that individuals and organization define their
security goals and policies as a first step toward achieving
a secure network.
- It is difficult to make such policies because it requires
- understanding the value of information, and
- the consequences of directing people to modify behavior.
- Aspects of protection:
- Data Integrity - protection from change
- Data Availability - does data remain accessible to legitimate
users?
- Data Confidentiality - protection against being viewed by
unauthorized persons.
- Privacy - preservation of rights to anonymity
- 29.4 Responsibility and Control
- Someone has to be assigned responsibility for the security of
each datum.
- There have to be clearly defined ways of authorizing access and
change to data that ensure the data are used according to policy.
- There have to be ways to authenticate the identities of those who
have the privilege of access.
- 29.5 Security Technology
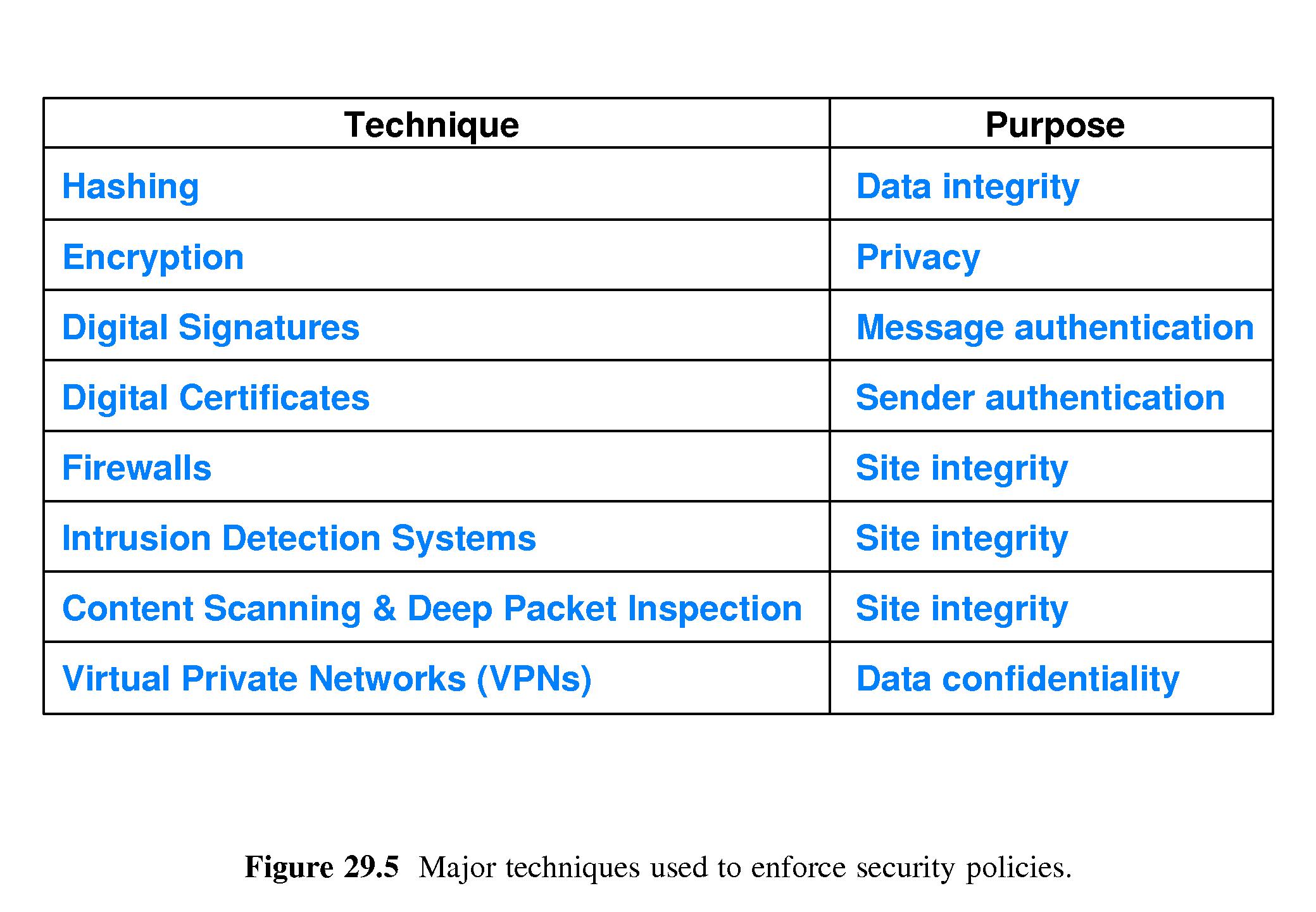
- 29.6 Hashing: An Integrity and Authentication Mechanism
- In one method, a sender S and receiver R share a secret key K.
- S creates a message M and executes an algorithm A to create
a short string H = A(M,K).
- S sends M and H to R.
- R runs the algorithm again to compute A(M,K). If the result matches
the value of H sent by the S then R concludes that M must be intact.
- If the message were changed in transit by a criminal, then it's
highly unlikely that A(M,K) would still match H.
- Since no one but S and R know K, it's also extremely unlikely that
someone could have changed M to M' and substituted H' = A(M',K) for
H.
- 29.7 Access Control and Passwords
- Care must be taken with passwords transmitted across a network.
- If passwords are not encrypted, anyone able to eavesdrop on the
network can learn them.
- It is relatively easy to eavesdrop, especially on a wireless network.
- It is also important to choose passwords that are not easy to guess.
- Software can be used to automate attempts to guess passwords.
- It's usually very easy for such software to guess a password that is
based on a name or a word in any dictionary (including slang and
obscure words).
- 29.8 Encryption: A Fundamental Security Technique
- Terms: plain text, cyphertext, encryption key, decryption key.
- Application of encryption function: C = encrypt(K1, M)
- Application of decryption function: M = decrypt(K2, C)
- 29.9 Private Key Encryption
- Two broad categories of encryption are private key encryption and
public key encryption.
- In private key encryption, two parties X and Y share a single secret
key K that is used for both encryption and decryption.
- The scheme is symmetric - either X or Y can send or receive and use
K to encrypt or decrypt.
- Obviously K has to be kept private because anyone who has K can
decrypt and encrypt with it.
- 29.10 Public Key Encryption
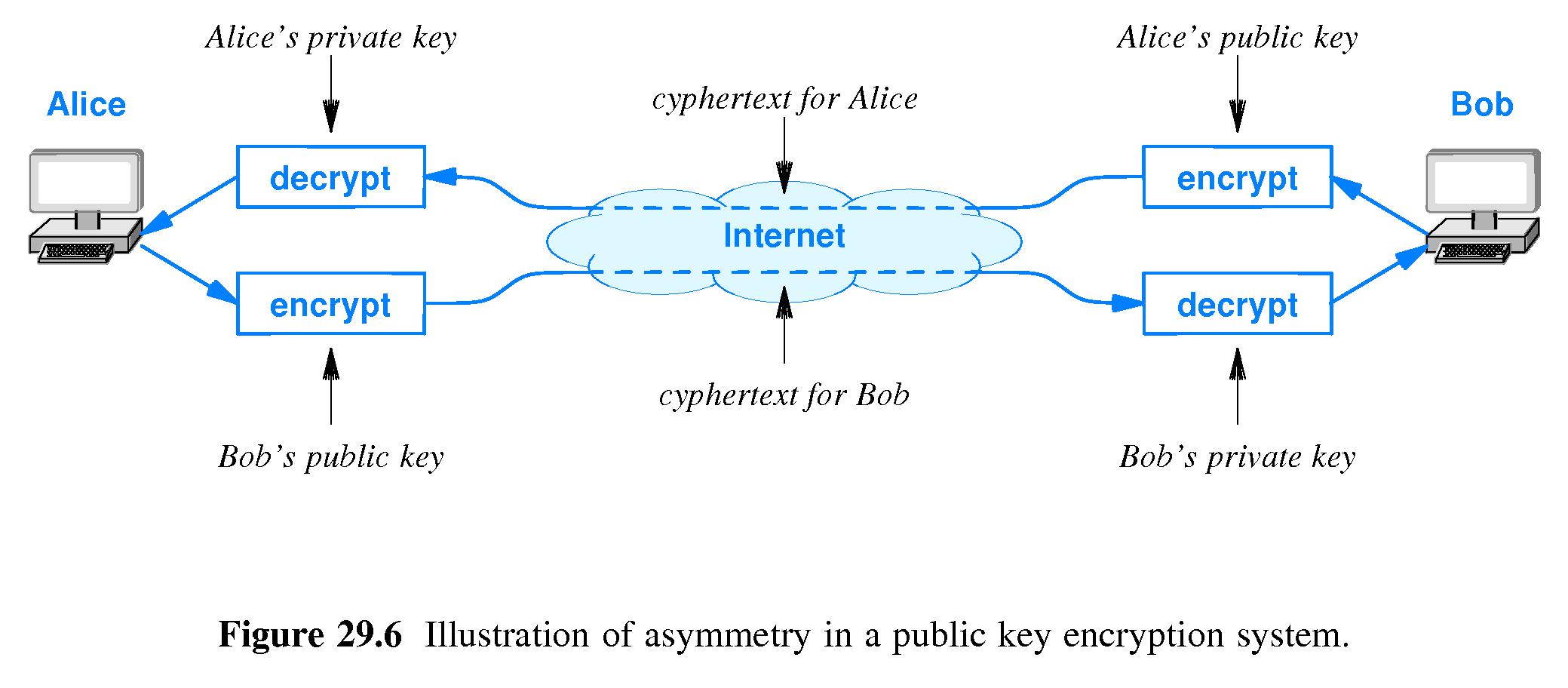
- Refer to Figure 29.6 on page 518.
- With public key encryption, each entity (let's say each 'person') who
wants to use encryption receives TWO keys. One is a public key
Kpub that may be published to the world. The other is a
private key Kpriv that must be known only to the person to
whom it is issued. (If X has a private key, he must not share it
with anyone - not even the people with whom he communicates.)
- A message can be encrypted using either Kpub or
Kpriv. A message that has been encrypted with
Kpub can be decrypted, but only by using Kpriv.
Similarly, a message that has been encrypted with Kpriv
can be decrypted, but only by using Kpub.
- If X is a person who wants to send a confidential message to Y,
here's how X can do it:
- First X uses Y's PUBLIC KEY to encrypt the message.
- Then X sends the encrypted message to Y.
- Then Y uses her PRIVATE KEY to decrypt the message.
- Since no one but Y has a copy of her private key, no one is able to
read the message as it passes through the network.
- 29.11 Authentication with Digital Signatures
- One may send a digital signature using public key encryption.
- If X wants to sign a message M, he encrypts it using his PRIVATE KEY.
- When Y, or anyone receives the encrypted message she attempts to
decrypt it with X's PUBLIC KEY. If the result is an intelligible
message, then Y has high confidence that the message came from X.
- The digitally-signed message is authenticated but not
confidential, since anyone with X's public key can view it.
- One may send a message that is both confidential and authenticated by
combining the schemes described above.
- The way it works: X wants to send a confidential, signed message to
Y. First X takes the plain text message M and applies his (X's)
PRIVATE KEY, to sign it. The result is an encrypted version M' of
M. Then X applies Y's PUBLIC KEY to M', which further encrypts it -
let's say the final result is M''.
- M'' is now confidential because only Y can transform it back into M'
by using her PRIVATE KEY. M'' is authenticated because only X's
PUBLIC KEY will transform M' back into M.
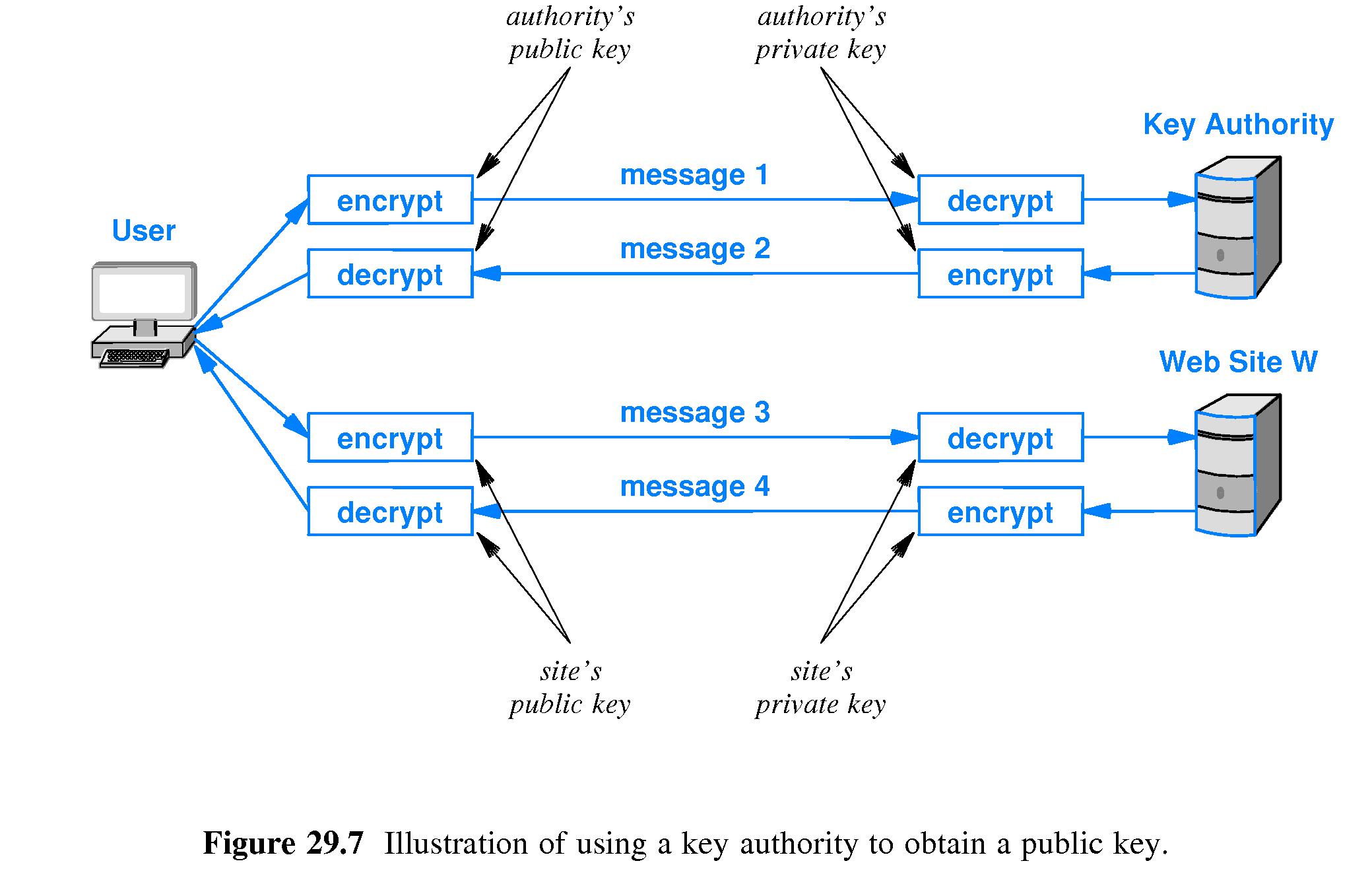
- 29.12 Key Authorities and Digital Certificates
- Refer to Figure 29.7.
- As the summary states, it's possible to create a secure key
distribution system that only requires manual configuration of
one public key.
- Suppose that X wants to access web site W in a secure manner.
- As the figure illustrates, if X has the PUBLIC KEY of a Key
Authority KA, X can send a confidential message to KA requesting
the public key of W.
- KA can then send W's PUBLIC KEY to X in a message M. KA can sign M
using its PRIVATE KEY. Thus, KA can send W's PUBLIC KEY to X in a
way that assures its authenticity. X knows that it is not using a
forgery of W's PUBLIC KEY.
- After X obtains W's PUBLIC KEY, it can engage in a secure
communication with W.
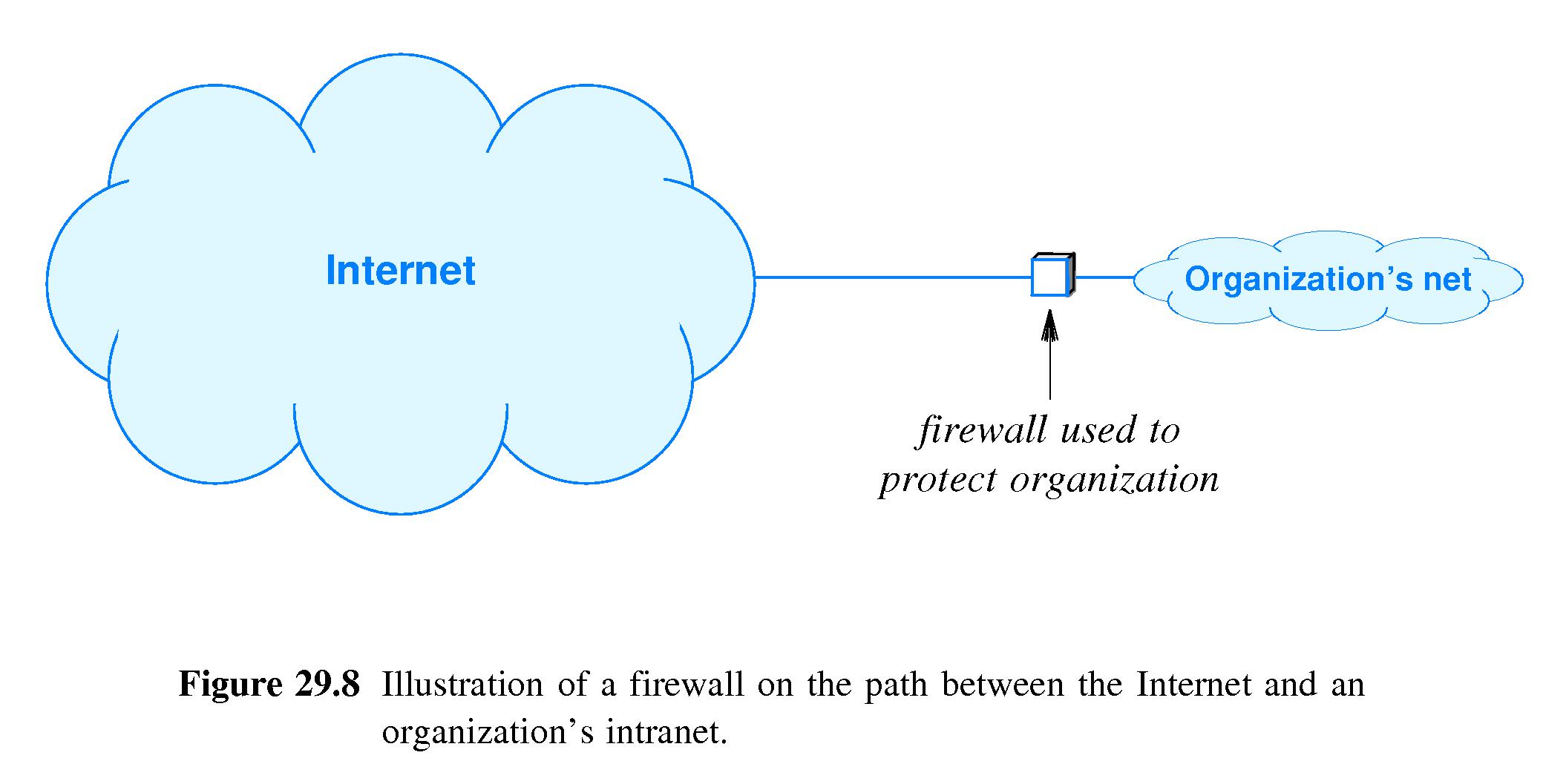
- 29.13 Firewalls
- Refer to Figure 29.8.
- An Internet firewall is a host F placed between two networks M
and N for the purpose of protecting N from M.
- F must be hardened against all forms of possible attack that might
come from M (or, for that matter, from N).
- F must examine all packets that pass between M and N.
- F must drop (refuse to forward) all packets it encounters that
are not in conformance with N's security policy.
- Administrators typically will not need to do very much to
harden hosts inside network N against attack, because F protects
them from external attack.
- F can make it difficult for:
- outsiders to probe N to discover N's topology and IP addresses
of N's hosts.
- outsiders to send excessive packets into N, or sequences of
packets known to be harmful.
- outsiders to send viruses into N.
- for insiders to send valuable data out of N.
- 29.14 Firewall Implementation with a Packet Filter
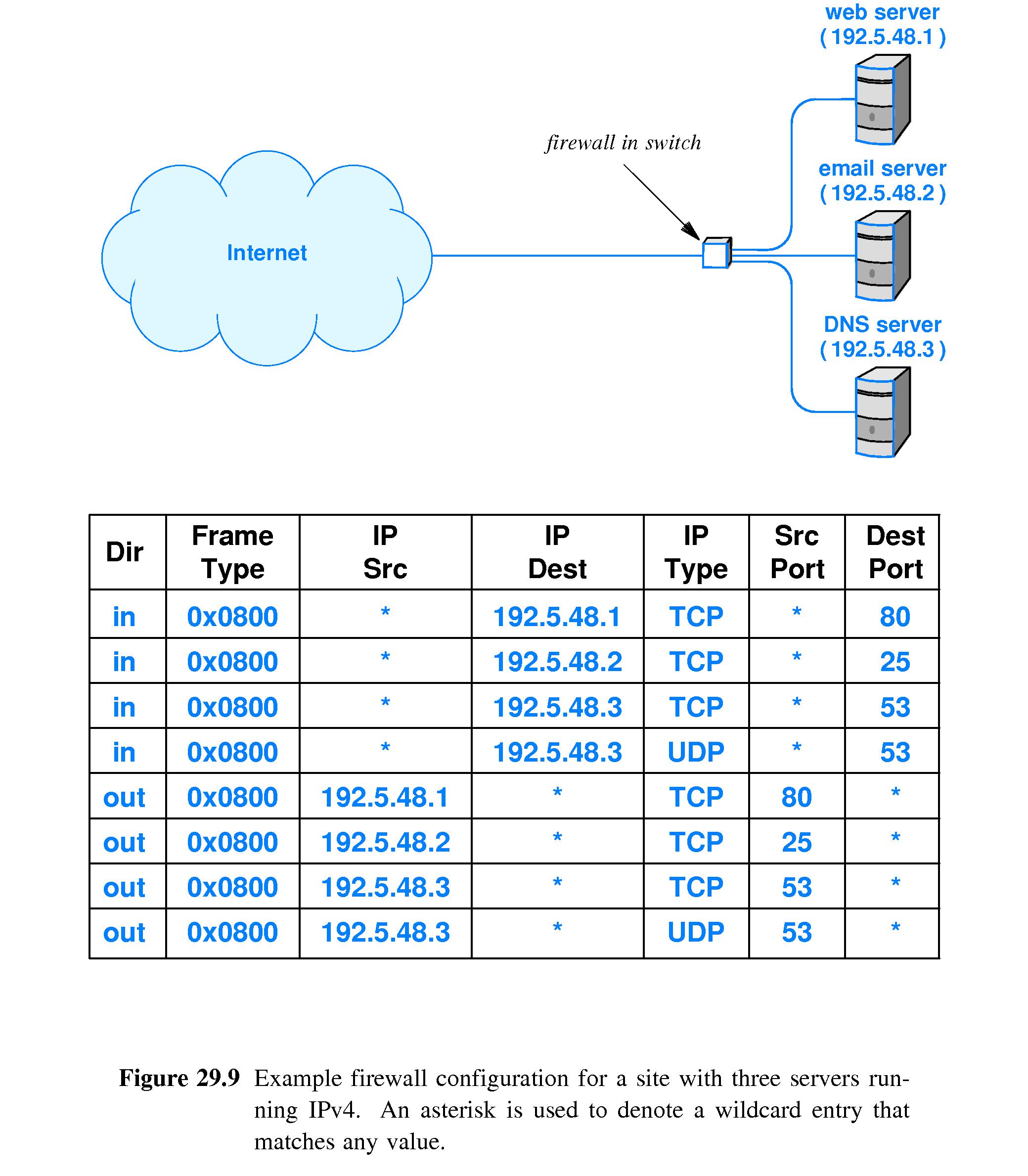
- Refer to Figure 29.9.
- Firewalls are typically embedded in a switch or router.
- Managers configure an on-board packet filter that decides
which traffic can pass through.
- For example, inbound traffic might be limited to clients connecting to
the web server on one machine, the e-mail hub on another machine and
the DNS server on a third machine.
- The packet filter must be configured to pass through the necessary
outbound traffic from the servers.
- Packet filters can screen packets based on a variety of
characteristics - usually characteristics of headers such as protocol
type, source address, destination address, datagram type or port
number.
- 29.15 Intrusion Detection Systems
- An IDS is software that monitors packets, attempts to determine when
a host or site is under attack, and take appropriate defensive
measures.
- Defensive measures taken by an IDS may include notification of a site
administrator and/or dynamically adding rules to the configuration of
a firewall to block the attacker's packets.
- An IDS typically can detect port scanning and SYN
flooding.
- Denyhosts is a simple IDS that can be deployed on a host to
detect dictionary-based password attacks and dynamically
configure the host to block attempts by the attacker to establish a
TCP connection with the host.
- 29.16 Content Scanning and Deep Packet Inspection
- File Scanning is familiar to many computer users - it is the
kind of examination that virus scanners perform - going through files
looking for signatures or fingerprints of known
viruses.
- Deep Packet Inspection (DPI) is similar, but can be performed
by a host or router on a low speed network. The inspection filter
checks the data payloads of network packets passing by in an attempt
to detect 'dangerous' contents.
- Our text gives the example of a datagram containing a domain name
known to be a security risk.
- 29.17 Virtual Private Networks (VPNs)
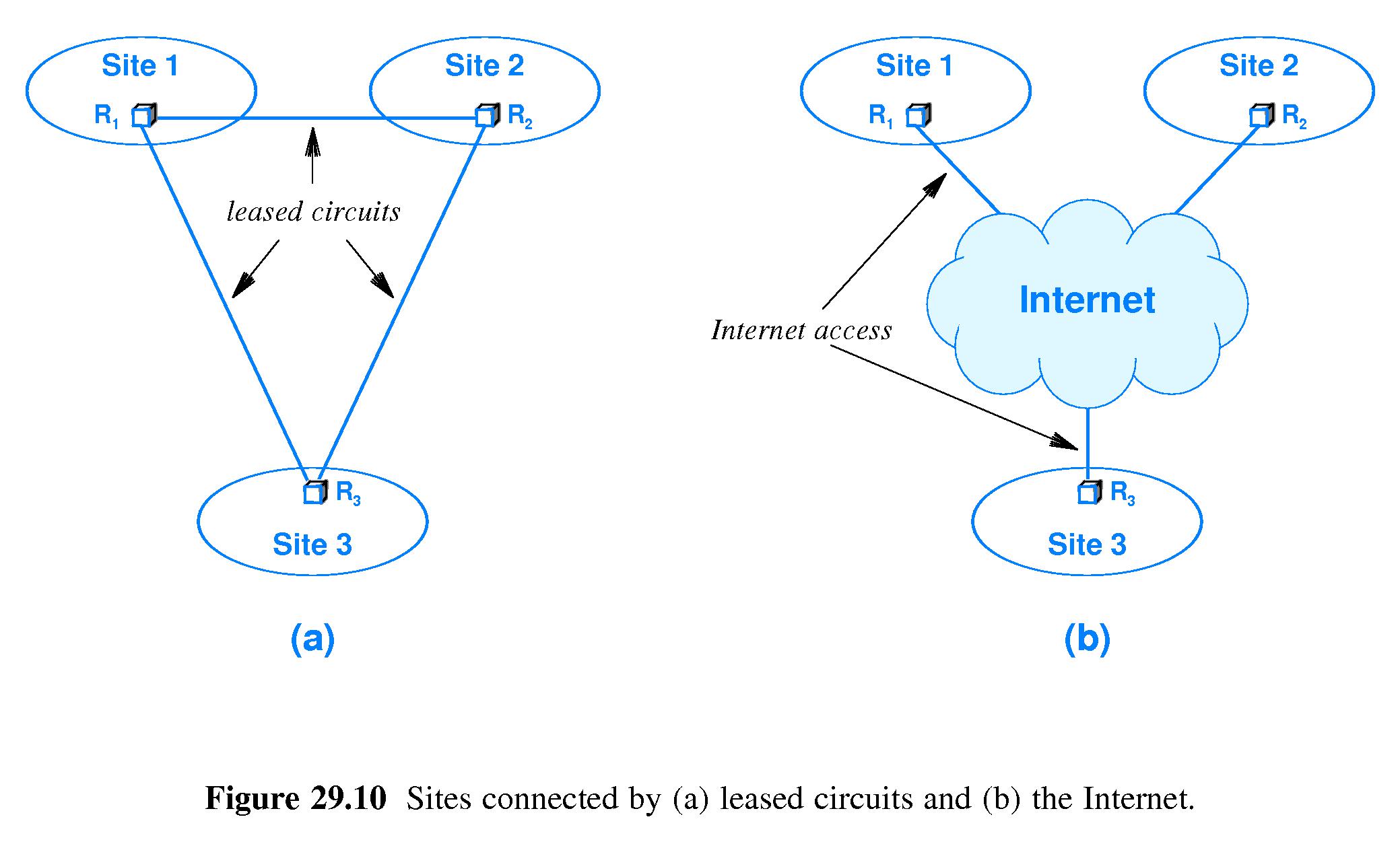
- Refer to Figure 29.10.
- VPN's are a common, effective, and cost-effective security
technology.
- Suppose there is an organization with three sub-units X, Y and Z,
each remote from the other two. For example they might be three
government laboratories that perform classified research.
- One way to insure that all communication between pairs of the sites
is confidential would be to lease private data lines that could only
be accessed by traffic between the sites. (Also they'd have to be
protected from wiretapping.)
- As a cost-effective alternative, the public Internet could be used to
send all the messages between the sites, but all that information
would be encrypted before leaving any of the sites.
- VPN's are set up with special gateways that do the encryption and
decryption automatically as packets cross them.
- VPN gateways are typically configured to perform firewall functions -
such as filtering out any incoming packet whose source is not one of
the other VPN gateways.
- 29.18 The Use of VPN Technology for Telecommuting
- The VPN technology may be used by individual telecommuting
employees.
- Basically, through the use of a small stand-alone device or VPN
software, they can set themselves up a small personal area network
using a VPN gateway to communicate with the other VPN gateways of the
organization.
- 29.19 Packet Encryption vs Tunneling
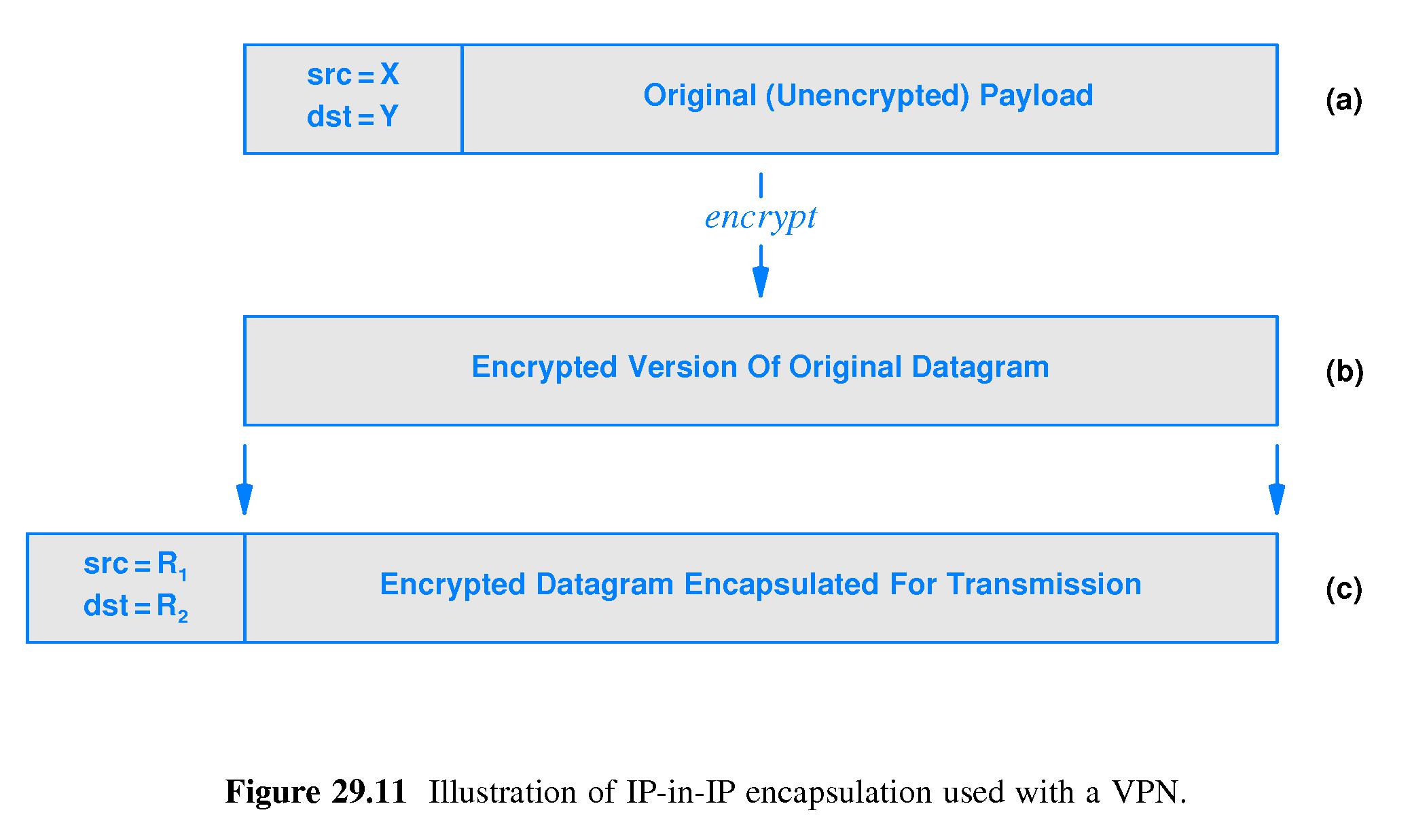
- Refer to Figure 29.11.
- There are various options for performing the encryption of packets to
be transmitted over the Internet:
- Payload Encryption
- Encrypts the payload only.
- Eavesdroppers can learn information in packet headers, such
as source and destination IP addresses and port numbers.
- Attackers may be able to infer other information by
noticing correlations between patterns of communications
and patterns of subsequent events, e.g. "stock goes up
after the CFO sends a short message to the CEO" or "stock
goes down after the CFO sends a long message to the CEO"
- IP-in-IP tunneling
- Encrypts an entire IP datagram, header and all, and ships
it inside another IP datagram.
- One VPN router performs the encapsulation and ships to
another. The IP addresses in the outer datagram are
addresses of the VPN routers.
- The advantage over payload encryption is that no addresses
or ports of hosts internal to the organization networks
appear in the unencrypted outer header.
- IP-in-TCP tunneling
- Like IP-in-IP encryption, except a TCP connection is used
instead of one-shot IP datagrams.
- TCP is used to send a stream of encrypted IP datagrams.
- Small added headers delimit datagram boundaries in the
stream.
- Advantage: reliable transport of TCP
- Disadvantage: If there is a problem with receiving one
segment, TCP cannot deliver data from successive segments
until the problem is resolved and the missing segment is
ready to be passed up the protocol stack.
- Potential problems with VPN's:
- Increased latency due to trips across Internet between VPN
routers.
- Decreased throughput because of use of the (slower) Internet
instead of a high-speed LAN.
- Increased overhead and fragmentation resulting from the use of
tunneling.
- 29.20 Security Technologies
- Pretty Good Privacy (PGP): Encrypt data before transmission.
- Secure Shell (SSH): Remote login protocol that encrypts what
is transmitted over the network.
- Secure Socket Layer (SSL): Authentication and confidentiality
for web-based financial transactions.
- Transport Layer Security (TLS): Successor to SSL, available
for use with HTTPS
- HTTP Security (HTTPS): Combines HTTP with SSL or TSL.
- IP security (IPsec): Security standard used with IP datagrams
to provide authentication and confidentiality
- Remote Authentication Dial-In User Service (RADIUS): Protocol
to provide centralized authentication, authorization and accounting -
popular with ISP's and VPN's.
- Wired Equivalent Privacy (WEP): Standard for keeping WiFi
transmissions confidential. Has weaknesses. Wi-Fi Protected Access
(WPA) is the replacement.










