(rev. May 01, 2015)
Notes On Chapter Twenty-Four
-- UDP: Datagram Transport Service
- 24.0 Study Guide
- Know what an end-to-end protocol is.
- Understand that UDP is an end-to-end, transport level protocol.
- Understand that UDP is connectionless, message-oriented, best-effort,
arbitrary interaction, and operating system independent.
- Know the kinds of applications that are well suited for UDP.
- Understand the role of port numbers in UDP.
- Know that UDP datagrams are encapsulated in IP datagrams, which are in
turn encapsulated in hardware frames.
- 24.1 Introduction
- The User Datagram Protocol (UDP)
- UDP as major transport-layer protocol
- UDP as connectionless service
- UDP packet format
- Applications of UDP
- UDP as best-effort delivery service
- Concept of protocol port numbers
- 24.2 Transport Protocols and End-to-End Communication
- IP is at layer 3 in the TCP/IP model.
- IP treats NICs as endpoints of communication - not processes
as endpoints of communication.
- In other words IP does not provide support for allowing executing
programs to communicate across the Internet.
- The transport layer (layer 4) contains the end-to-end protocols that allow
processes (a.k.a. applications, a.k.a executing programs) to communicate.
- Port addressing enables process communication. Port addressing
is handled at the transport layer.
- 24.3 The User Datagram Protocol
- UDP Characteristics:
- End-to-End: able to distinguish among applications
executing on a given host.
- Connectionless
- Message-oriented: applications send and receive
individual messages. (Basically, UDP provides a means for
applications to send and receive individual IP datagrams.)
- Best-effort - same best-effort service as IP.
- Arbitrary Interaction: applications can send to many,
receive from many, or communicate with exactly one other
application.
- Operating System Independent: The port-number scheme is
independent of differences among operating system schemes for
identifying processes.
- 24.4 The Connectionless Paradigm
- No set-up or tear-down
- Communication consists only of UDP messages
- Send anytime
- No maintenance of "state"
- Low overhead
- 24.5 Message-Oriented Interface
- UDP protocol software merely sends and receives single UDP messages
(called user datagrams).
- Each UDP message is individually encapsulated in an IP datagram.
- The protocol does not support dividing long UDP messages and
sending them in multiple IP datagrams, or packing groups of
short messages into single datagrams.
- If an application attempts to send a UDP message that is too large
for the path MTU, it will be fragmented by IP protocol software,
quite possibly on the sending host. This is not efficient
use of the network.
- Most path MTUs are at least 1500 octets, so programmers typically
try to keep UDP message sizes under about 1400 octets.
- 24.6 UDP Communication Semantics
- UDP simply relies on IP for delivery.
- Accordingly a UDP message can be lost, duplicated, delayed, delivered
out-of-order or corrupted.
- If applications need additional error detection and correction
measures the programmers who create the applications have to provide
them.
- It's often appropriate to use UDP with applications like streaming
audio or video, since those applications can well tolerate
transmission errors such as occasional packet loss.
- 24.7 Modes of Interaction and Multicast Delivery
- UDP can use IP broadcast and multicast services.
- 24.8 Endpoint Identification with Protocol Port Numbers
- Hosts use protocol port numbers to identify executing
applications
- Hosts have to map between port numbers and whatever identifiers the
host operating system uses to identify processes. (e.g. unix has its
PID system.)
- For example an echo server is supposed to accept connections on port
7. So when a packet arrives addressed to port 7 on a host, the host
has to somehow pass the packet to the echo server process.
- Support for 1-1 communication:
A process R can tell UDP that it only wants to receive UDP messages
from a specific process S on a specific host. The feature is
implemented like this: into the socket
R uses to communicate, it places the IP and protocol numbers of S.
UDP software then only passes UDP messages with source address
and port matching S.
- Alternatively, R can tell UDP to pass through messages from any
host.
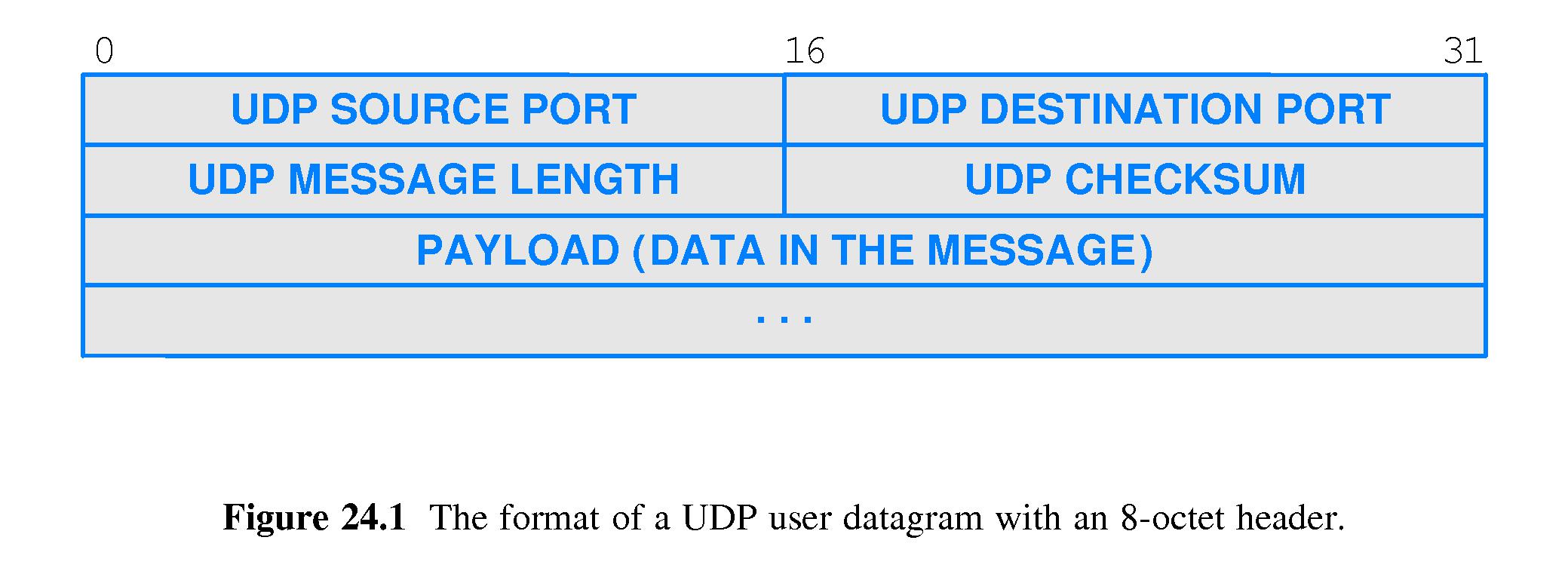
- 24.9 UDP Datagram Format
- The UDP message is called a user datagram
- The user datagram header is very simple: fields for source and
destination ports, UDP MESSAGE LENGTH, and an optional checksum.
- 24.10 The UDP Checksum and the Pseudo Header
- The UDP header does not contain IP addresses.
- The optional UDP checksum is calculated including pseudo header
information - the UDP message length and, from the encapsulating IP
datagram, IP source and destination addresses, and type field.

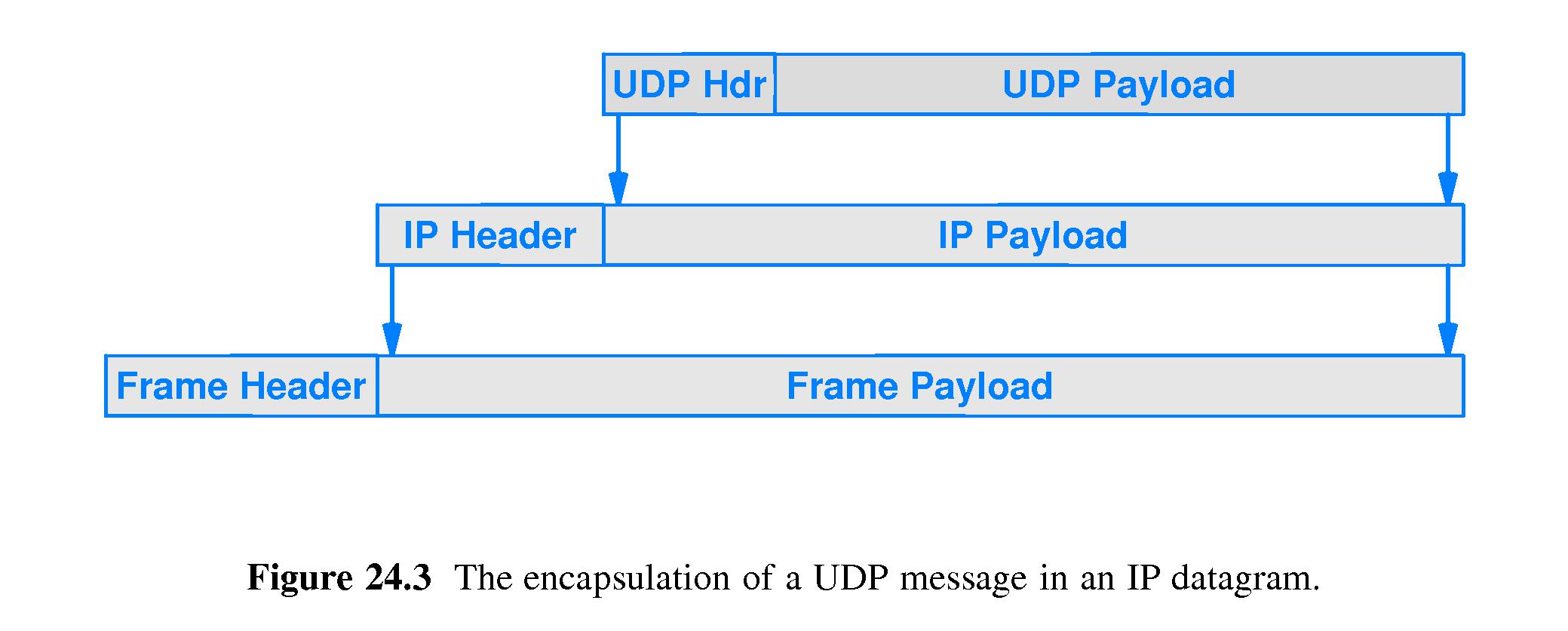
- 24.11 UDP Encapsulation
- When traveling over a network, a UDP user datagram is encapsulated
inside an IP datagram, which in turn is encapsulated inside a
physical network frame.
- The cumulative nature of the encapsulation that occurs as information
moves down a protocol stack is in contrast to the style of
encapsulation that happens as routers forward IP datagrams
along the Internet. Each router removes the IP datagram from its
encapsulating frame, discards the frame, and places the IP datagram
in another frame for forwarding to the next hop destination.