(rev. 01/13/2008)
Notes On Chapter Twenty-Four
-- UDP: Datagram Transport Service
- 24.1 Introduction
-
This chapter discusses:
- UDP Packet Format,
- Applications of UDP, and
- Protocol Port Numbers
- 24.2 The Need For End-to-End Transport Protocols
- IP datagrams have address fields only for the source and destination
hosts.
- Multiple programs may be running on a host.
- UDP is an end-to-end protocol (transport
protocol) that allows individual application
programs (processes) to communicate.
- IP is not an end-to-end protocol.
- 24.3 The User Datagram Protocol
-
UDP characteristics are:
- End-to-end.
- Connectionless
- Message-oriented
- Best-effort
- Arbitrary interaction - [send to or receive from any
application(s)]
- Operating system independent - [identify a process without
using the "pid's" used by the local OS]
- 24.4 The Connectionless Paradigm
- UDP is "one-shot" communication - like sending
a postcard.
- No connection setup or tear-down.
- No control messages.
- Low Overhead
- 24.5 Message-Oriented Interface
- Each UDP packet is distinct - packet boundaries
are preserved - receivers have no problem knowing where the
data from one UDP packet ends and another starts.
- UDP can lead to inefficient use of the network.
- The ratio of header to payload may be high.
- Large UDP packets may be fragmented - even on the sending host.
- 24.6 UDP Communication Semantics
- UDP uses IP for delivery
- Delivery problems may occur
- Applications must be immune to delivery problems, OR
- Programmers must add code to handle such errors
- 24.7 Arbitrary Interaction
-
UDP allows four styles of interaction:
- 1-to-1
- 1-to-many
- many-to-1
- many-to-many
- 24.8 Support For Unicast, Multicast, and Broadcast
- UDP packets may be encapsulated in IP broadcast
or multicast packets.
- 24.9 Endpoint Identification With Protocol Port Numbers
- UDP identifies source and destination processes
using port numbers
- Each OS provides a mapping between port numbers and local process
identifiers.
- "Standard" servers listen for clients on
well-known port numbers. (e.g. timeserver on port 37)
- An application using UDP can specify a
particular remote host and port from which to accept datagrams,
OR
- An application using UDP can accept packets
from any host and port.
- There's an example in chapter 29 that shows how to specify port
numbers using the socket API.
- 24.10 UDP Datagram Format
- The UDP packet is called a user datagram.
-
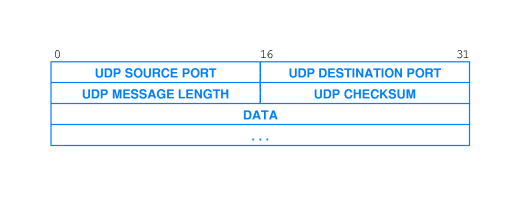 The format of a user datagram is as shown at right.
The format of a user datagram is as shown at right.
- 24.11 The UDP Checksum And The Pseudo Header
- The UDP checksum is optional.
- There is no place in the user datagram for IP
addresses - they go in the header of the encapsulating IP
datagram.
- As a guard against possible errors at the IP level, UDP
incorporates certain fields from the IP header into the
UDP checksum:
- source IP address,
- destination IP address, and
- IP type field.
- 24.12 UDP Encapsulation
-
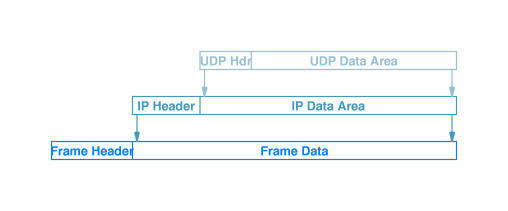 The figure at right illustrates encapsulation
of a UDP user datagram.
The figure at right illustrates encapsulation
of a UDP user datagram.
- 24.13 Summary
 The format of a user datagram is as shown at right.
The format of a user datagram is as shown at right.
 The figure at right illustrates encapsulation
of a UDP user datagram.
The figure at right illustrates encapsulation
of a UDP user datagram.