(rev. 01/01/2008)
Notes On Chapter Two
-- Motivation and Tools
Chapter Two: Motivation And Tools
- 2.1 Introduction
- 2.2 Resource Sharing
- People want networks so they can share printers, share files, share
powerful CPU's.
- At the time that the Internet got its start, the sharing of powerful
computers was important to researchers working at government
laboratories.
- The Department of Defense is also said to have been interested in
developing a network that could continue to function even after
being heavily damaged.
- ARPA put together a large group of the best and brightest
individuals available and they created the Internet. The story
has something of the flavor of the story of the Manhattan
project.
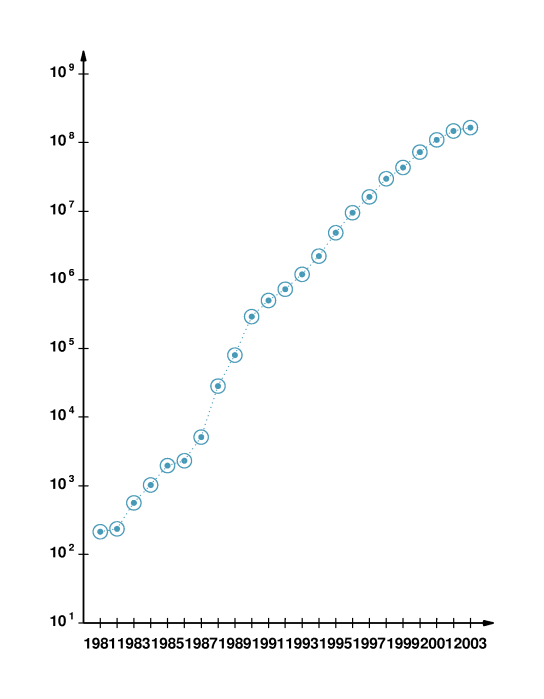
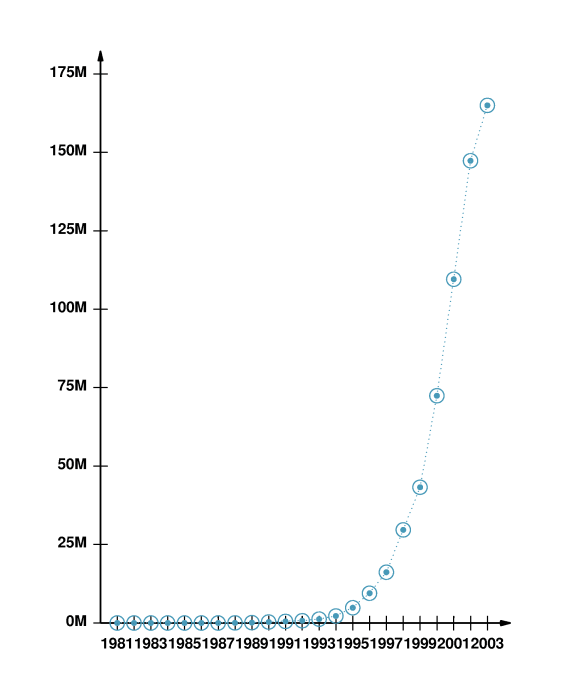
- 2.3 Growth of the Internet
- Plots show that the number of hosts (computers) on the Internet
approximately doubled every 9-12 months from 1981 through 2003.
- What has been the relative growth in various areas of the world?
- 2.4 Probing the Internet -- use of ping
- Who keeps track of how big the Internet is getting, and how do
they do that? Nowadays it is done using DNS queries, ping, and
statistical sampling techniques. Check out details here: Internet Software Consortium
- Everybody who troubleshoots Internet connections should know about
ping. It is the first tool you use to see if you can reach a
host from where you are. (Do a demo of ping.) Ping is basically
just an echo-response test. You send a packet to a host, and it
replies by sending a packet back to you.
- Ping command: ping altair.csustan.com
- Ping command: ping -s altair.csustan.com
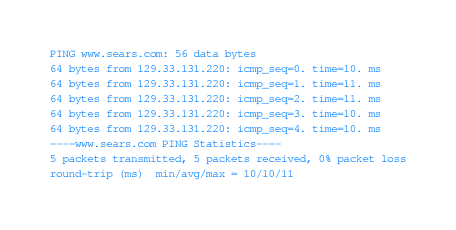
- 2.5 Interpreting A Ping Response.
- It can be hard to tell what is the reason for a failure. A link
could be down, a host could be down, software on the host could
have failed, software in the target network could be configured
to refuse to reply to ping requests.
- What is a scenario that illustrates the use of ping? If your
local host is having troubles and you know which remote hosts it
depends upon for services, you can ping all those remote servers
to see which one(s) your local machine is having trouble
reaching. This helps point you in the direction of what needs to
be fixed.
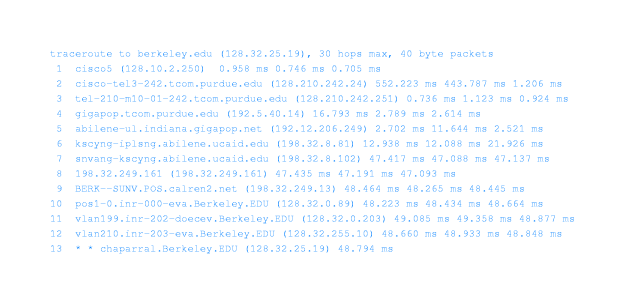
- 2.6 Tracing A Route -- do a demo of use of the traceroute utility
- When you send a packet from computer X across the Internet to
computer Y, it usually travels through a series of other
computers (routers) along the way. You can use traceroute to
identify those intermediate computers.
- Some of the routers may not respond to traceroute and therefore
traceroute may not discover all of them.
- Although routes tend to be pretty stable over short time spans,
two packets sent from X to Y may travel different routes at
different times. The information obtained from traceroute can be
misleading.
- 2.7 Summary
- Flavors of Unix include ping, traceroute and other network utilities
in their system software distributions.
- Personal computer users may not have these utilities "built-in."
However, one can download software packages that include ping and
traceroute, or one can get access to ping and traceroute servers on
the world wide web. Search
- Search TUCOWS for ping
software.
- If you want a web-base ping or traceroute server then look at
this
SLAC page
-
Network-Tools
-
Just-Ping



