(Latest Revision:
Fri May 18 00:27 PDT 2007
)
Notes On Chapter Forty
-- Network Security
40.1 Introduction
- This chapter describes network security
problems, along with criteria for solutions and techniques
for solutions.
40.2 Secure Networks And Policies
- An organization has to define the kinds of
network accesses that it wants to allow and deny.
- The network is secure when the
organization can insure that its access rules are followed.
- Complete security depends on protecting every avenue of access to
sensitive data -- not just network access.
- It is difficult to know the value of information.
- Lack of understanding of the value of information can lead to
poor understanding of what types of access should be allowed and
denied.
40.3 Aspects of Security
- Some of the aims of a security policy may be:
- Data Integrity -- protect data from
undesired changes
- Data Availability -- prevent loss of
access to data that we wish to be available.
- Data Confidentiality -- prevent persons
from seeing data without proper permission.
- Privacy -- keep secret the identities of
communicating parties.
- Often enforcing such aspects of security imposes "rules" on users
that make the system less convenient. One rule of thumb is: "Convenience is inversely proportional to security."
40.4 Responsibility And Control
- To have security, an organization must exert control over access
to data.
- Someone must be responsible for each datum
and keep records on how it is accessed.
- There must be clear policy regarding where data will be kept and
how access to it will be regulated and delegated.
40.5 Integrity Mechanisms
- To assure that a message has not been altered
during transmission, the sender can use a secret key (known
only to the sender and receiver) to create a
cryptographic hash of the message.
- The sender transmits the hash along with the message.
- The hash is like a checksum computed with a
secret recipe. Without the key, anyone who modifies the
message does not know how to modify the hash correspondingly.
- The receiver checks the authenticity of the message by computing
the hash again and comparing with the copy received with the
message.
40.6 Access Control And Passwords
- When a user enters a secret password at a computer console it is
a rather secure scheme.
- When a user enters a secret password to login remotely over a
network it is not nearly so secure. It can be easy for someone
to eavesdrop on the network and learn the password.
40.7 Encryption And Confidentiality
- One way to secure data sent over a network is
to encrypt it with a secret key: if you know the key you can encrypt
or decrypt.
- Some codes work like this: there is one key
that is used to encrypt and decrypt. The key has to be kept
secret. There is a problem of finding a secure
way to distribute the key to those who need to use it. (It
would seem we need another code for encrypting keys
before we send them in messages. However we then have to
figure out how to securely distribute the keys for the other
code. How do we escape from the "infinite recursion" of the
problem?)
40.8 Public Key Encryption
- It can be a problem to keep the secret key a secret.
- Public key encryption helps solve this problem.
- Each code has two keys: a public key that
everybody may know, and a private key that is kept secret.
- There is a relatively simple algorithm for
creating such codes. Software can do all the "math"
required. The software can also "randomly"
generate new codes. The number of possible codes is potentially
infinite.
- If Alice wants Ralph to send her a private
message, Alice can create a "random" public key code. She sends
Ralph a copy of the public key ( "in the clear" -- it doesn't matter
who sees that public key). Ralph encrypts his message using the
public key and sends the coded message to Alice. Alice decrypts it
with her private key -- which she never had to share with anyone.
Eavesdroppers who may have the public key cannot decode the
message -- there is no known practical way to decode the message
unless you know the private key.
- If Alice wants to send private information to Ralph, then Ralph can
create a code and send Alice the public key and they just work the
scheme in the other direction.
40.9 Authentication With Digital Signatures
- There's another use for the code: the
properties of the code are such that if the public key can decode a
message then it is all but certain that the message was encoded by
the private key. Therefore if Alice wants to
send a (not secret) message to Bert and wants him to be certain that
it really came from her (maybe Bert is her broker and she is
telling him to sell some stock for her) she
encrypts her message with her private key. Then if Bert can
decode the message with the public key he knows the message really
came from Alice. (Alice is the only person who has the private
key.)
- "Replay" by eavesdroppers is a potential threat, so the message
should contain the time and date.
- By combining the two schemes one can send
secret messages in such a way that the recipient will be certain who
the message came from.
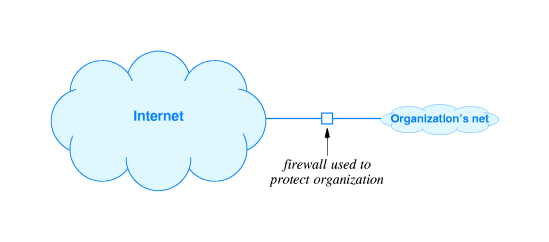
40.10 Internet Firewall Concept
- We can protect a network from undesired traffic
with one or more firewalls. To protect a network X from a
network Y every connection between X and Y must go through a
firewall.
- The firewall itself must be highly secure
-- immune from security attack.
- The firewall examines each packet that is sent
through it in either direction. It allows only desired traffic.
- In particular, a firewall can refuse to allow outside computers
(possible hackers) to communicate with insecure computers inside the
organization. Outsiders may be allowed to communicate only with
highly secure insider machines.
- It can be convenient and cost-saving to use firewalls because one does not have to make all the computers inside
the organization highly secure.
40.11 Packet Filtering Using Ports
- A packet filter is basically a router that
blocks some packets.
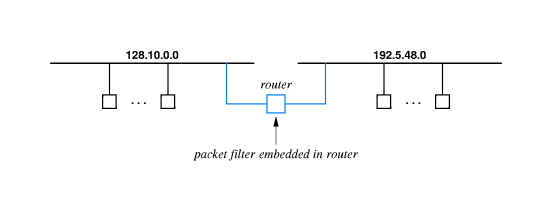
- The administrator sets up rules based usually on Boolean expressions
involving fields in IP packet headers.
- For example the filter can block all packets coming from a certain
source address, or block all FTP packets going to a certain
destination address.
40.12 Using Packet Filters To Create A Firewall
- In a firewall, devices that do ingress (incoming) filtering and
egress (outgoing) filtering may be separate.
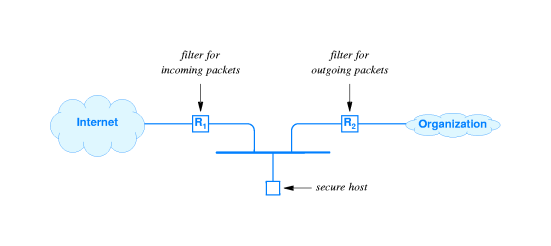
- There will be a secure host component that is
logically between the ingress and egress packet filters.
- Application software on the secure host will perform proxy services such as proxy FTP for internal
computers. For example the proxy FTP software would check downloads
for viruses before passing them along to the internal clients.
40.13 Virtual Private Networks
- VPN edge routers will send along traffic only if it is addressed
to another part of the VPN.
- All of the VPN traffic is encrypted while in transit across the
public parts of the network (e.g. the Internet).
40.14 Tunneling
- The IP packet must have a source and
destination address that is not in code while traveling across the
public Internet. This can be a problem because
eavesdroppers may be able to learn things about the company just
from looking at this information and other information in headers.
- The VPN may use IP-in-IP tunneling to keep header information such
as source and destination addresses confidential.
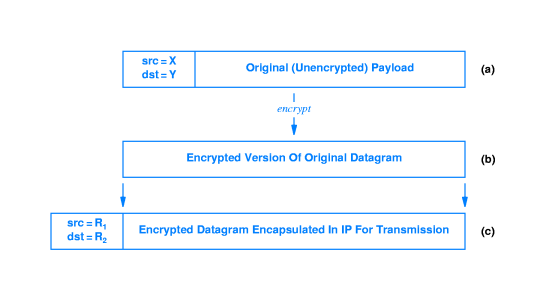
- When a packet gets to an edge router R1 on the VPN, R1 encrypts the entire packet including header, and
encapsulates it into another IP packet. The outer packet has source
address R1 and destination address R2 -- R2 being the edge router
where the packet is supposed to reenter the private part of the
network.
- When the packet gets to R2, R2 takes the inner IP packet out of the
outer IP packet, decrypts it and sends it on its way within the
private part of the VPN.
40.15 Security Technologies
- Intrusion Detection System (IDS) -
monitors all arriving packets and raises alarms.
- Pretty Good Privacy (PGP) - encrypts for
transmission
- Secure Shell (ssh) - like telnet, except
with encryption of data transmitted, including logon
password.
- Secure Socket Layer (SSL) - places an
encryption/decryption layer between a socket and the
application using it.
- IP security (IPsec) - a standard for
encryption of IP packets.
- Remote Authentication Dial-In User Service (RADIUS) - secure dialup service.
- Wired Equivalent Privacy (WEP) - a weak
encryption standard for wireless networks - replaced by
Wi-Fi Protected Access (WPA)
40.16 Summary




