(Latest Revision:
Sun Mar 11 17:19:43 PDT 2007
)
Notes On Chapter Fifteen
-- Network Characteristics: Ownership, Service Paradigm, And Performance
- 15.1 Introduction
- This chapter helps us learn to further characterize networks in
terms of ownership, services provided, and quality of
performance. These ideas will be revisited when we study the
Internet protocols.
- 15.2 Network Ownership
- Companies and individuals can own a
private network
- Many small and large companies have private LAN's.
- Many large companies have private WAN's.
- Private WAN's use leased lines from common carriers for long
haul point-to-point links because there are many
restrictions on where a private company can string wires.
- Advantages: It is relatively easy for the owners of a
private network to maintain tight control over its design,
traffic, hardware, software, and security.
- Disadvantages: a private network can be very expensive to
create, manage, and maintain -- especially a private WAN.
- A so-called public network
is a network owned by a common carrier that allows
any member of the public to connect for a fee.
- Public networks are typically always WAN's because there is
not much incentive to subscribe to a LAN. Users want to be
able to communicate with as many other users as possible.
Ideally, everyone on earth would be reachable.
- The "public" in public network does not imply that there
can be no privacy of communications.
- Advantages: Flexibiltiy -- anybody can communicate with
anybody; Cost -- expenses are shared among many users and
the common carrier is responsible for most of the expert
management and maintenance.
- Disadvantages: the lack of control enjoyed by
owners of a private network. (See above.)
- 15.5 Virtual Private Networks
- The concept of a virtual private network
(VPN) is to implement a private network using the facilities of
a public network in much the same way that one data
structure can be used to implement another data structure.
- Each private LAN connecting to the public part of the network is
equipped with a special edge router
(packet switch) that rejects all incoming or outgoing packets that
do not belong to the VPN.
- 15.6 Guaranteeing Absolute Privacy
- A VPN is not truly private because the long haul data lines and
packet switches are shared among arbitrary subscribers. For example
the packets corresponding to the communications of two hostile
companies might travel together through the same switches and
communication lines.
- To maintain privacy all packets are encrypted
during transit across the public part of the network.
- 15.7 Service Paradigm
- Networks typically offer high-level services and hide low-level
implementation details.
- Network services may be
connection-oriented (CO) or
connectionless (CL).
- The CO and CL terminology can be applied both to the high-level
services and the low-level implementation.
- A packet switched network like those we have been discussing can
support either type of service or both.
- Read the Unix man page on the socket command to learn more about
TCP/IP connection-oriented and connectionless services.
- 15.8 Connection-Oriented Service Paradigm
- Connection-oriented service
works a lot like telephone service:
- When host X desires to communicate with host Y, X makes a
request from the network to establish a connection to Y.
- Y has the option to accept or reject the
connection.
- If Y agrees to the connection the network system reserves a
data path between X and Y and signals them that they can now
communicate.
- X and Y communicate as long as they desire.
- Each can send information anytime it wants.
- Often either party is free to send any amount of data any time
it wants -- if there is a need, lower level software
transparently packetizes the data for transmission.
- Either party can request that the connection be closed at
any time, which puts an end to their communication until
they establish another connection in the future.
- 15.8.1 Continuous And Bursty Traffic
- Connection-oriented networks for voice or video typically
deliver continuous data at a fixed rate
- Connection-oriented data networks handle bursty traffic.
- 15.8.2 Simplex and Full Duplex Connections
- Full Duplex: Each connection allows two-way communication
- Simplex: A separate connection is required for
each direction.
- 15.8.3 Connection Duration And Persistence
- Permanent Connections
- may be created with manual switch settings and/or records
on disk
- may persist over months or years
- may persist over system reboots
- Switched Connections
- are dynamic
- typically persist only for the duration of a session
- 15.8.4 Service Guarantees
- Minimum Throughput Rate
- Average Throughput Rate
- Maximum Packet Loss
- Maximum Delay
- 15.8.5 Stream or Message Interface
- A connection may provide a
stream interface
- Users are unaware of packets or other data boundaries.
- An application can send any number of bytes at any time.
- Receivers may request any number of bytes at a time
- Other connections have a
message interface
- the network delivers data in units the same size
transmitted by the sender.
- 15.9 Connectionless Service Paradigm
- Connectionless service works a
lot like post office mail service:
- The sender places source and destination addresses
and data in a packet.
- The sender turns the packet over to the network
system for delivery.
- 15.10 Interior And Exterior Service Paradigms
- Networks operate at various levels.
- A network can offer a connection-oriented service at one
level (e.g. a connection-oriented service made available to the
computers using the network). However that service may be
implemented using a connectionless interface at a lower
(internal) level.
- Conversely, one can implement connectionless service using
connection-oriented facilities at a lower level.
- 15.11 Comparison of Service Paradigms
- Advantages, Disadvantages, and
Characteristics of Connectionless and Connection-Oriented
services
- It is easy for service providers to keep track of how long a
connection remains open, and to charge the user "by the
minute."
- There is usually a "flat rate" for connectionless service.
(unlike postal service).
- The network can usually tell applications (programs) using a
network connection that their connection has been broken.
The applications can then take appropriate measures to
recover or make a log entry about the problem.
- When there is a link failure between hosts using a
connectionless service, it may take a long time before it
becomes apparent that communication is no longer working.
- Holding a connection open may waste resources.
- If the amount of information to be sent is small, the time
spent opening the connection may be longer than the actual
transmission time for the data.
- When communication proceeds in a sporadic series of short
bursts, connectionless service is often more economical than
connection-oriented service.
- 15.12 Examples of Service Paradigms
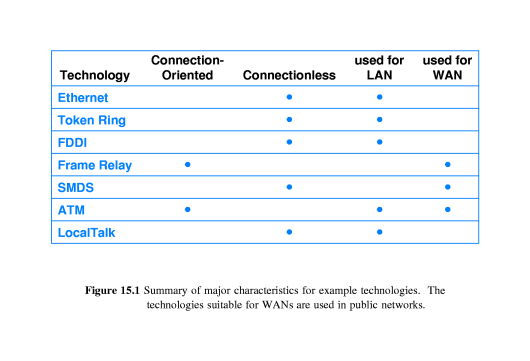
- Frame Relay is connection-oriented
(both switched and permanent connections are available).
Connectionless service is not available with Frame Relay.
- SMDS is connectionless
- ATM is connection-oriented (both
switched and permanent connections are available).
Connectionless service is not available with ATM.
- 15.13 Addresses and Connection Identifiers
- When two hosts set up a connection to communicate, usually the network system will assign a small integer value
called a connection identifier to the connection.
- When one of the hosts wants to send data, it just uses the
connection identifier to specify what "pipe" to send the message
through -- there is no need to give the
address of the recipient.
- On the other hand, when a packet is sent
over a connectionless network, it has to carry the destination
address.
- The advantage of using a (small) connection identifier instead of
a (large) address is that it means packet headers can be smaller
-- increased effective bandwidth.
- (Those familiar with the concept of an open file descriptor
will see an analogy with the idea of the connection identifier)
- (Those familiar with distributed file system concepts will note
that connection-oriented service is stateful while
connectionless service is stateless.
- 15.14 Network Performance Characteristics
- 15.14.1 Delay
- Delay in a network refers to
the time it takes for a signal to move through a part of the
network.
- Delay is measured in seconds or fractions of a second.
- Propagation delay is the time it takes for a signal
to move from one end of a communication line to the other.
- Switching delay is the amount of delay experienced by
a packet as it moves through a switch.
- Wait time for network media to become available (e.g. token
ring or ethernet) is called access delay.
- Queueing delay is the time packets wait in queues
on packet switches. This delay is in addition to switching
delay.
- 15.14.2 Throughput
- If we think of a network link as being like a pipe with bits
flowing through it, then the
throughput is the number of bits per second emerging
out the end of the pipe.
- Effective throughput is the amount of useful data
(payload) emerging from the pipe in bits per second.
Headers and check sums don't count as useful.
- Throughput is measured in bits per second.
- 15.14.3 The Relationship Between Delay and Throughput
- In theory throughput and delay are independent.
- If you just make a pipeline wider you can increase the
throughput without changing the delay.
- If cars travel 60 mph on two west-bound lanes, you can
get more throughput if the cars travel closer together.
- In practice, measurements show that
network delay tends to be inversely proportionate to unused
channel capacity:
D = D0/(1-U)
- The delay is lowest when there is very little traffic on the
channel.
- Delay increases moderately when the amount of traffic
increases from near zero to moderate amounts of traffic.
- Delay increases dramatically when the amount of traffic
increases from moderate amounts of traffic to near maximum
amounts of traffic.
- Opinions vary about how high network managers should allow
utilization to get. The text mentions values from less than
50% to 80%.
- 15.14.4 Delay Throughput Product
- If the throughput of a link is T bits per second then the
amount of bits that will come out of
the link in n seconds is (T * n) bits.
- If n happens to be the delay from end
to end of the link, then since all the data
currently contained in the link will emerge in n seconds,
(T * n) also represents the amount of
data currently contained in the link.
- If 125,000 liters per second of water flows out of a pipe, and
the end-to-end delay is 321 seconds, how much water is in the
pipe? Answer: 125,000*321 = 40,125,000 liters.
- 15.15 Jitter
- The jitter in a network is the
variance in delay.
- 15.15.1 Isochronous Networks
- In an isochronous network, each bit
or packet takes exactly the same time to travel across the
network.
- 15.15.2 Asynchronous Networks
- A network that has jitter is called asynchronous.
- "Additional protocols" can be used to send audio and video
successfully across an asynchronous network.
- An isochronous network is best for audio and video but (so
far) significantly more expensive than an asynchronous
network.
- 15.16 Summary
